Unattended Remote Access: Top Use Cases, Benefits, and Main Aspects
Unattended Remote Access is the ability to access a remote computer without requiring someone at the destination computer to grant access. You have full control of the computer in real-time.
This article will explain the concept of unattended remote access, what it is, and why it is a useful tool in any business. You will also be introduced to some software options available to make unattended remote access possible.
What Is Unattended Access?
You may already be familiar with remote desktop – unattended remote access takes this traditional concept one step further by allowing remote access to a computer when there is no end-user physically located at the remote computer. This is a useful addon to your business arsenal of tools as it allows your employees to log in and access files at any time and from anywhere. Alternatively, IT support teams can perform 24/7 remote support tasks like remote software installations, or after-hour fault finding etc.
Some examples of remote unattended access software include LogMeIn, TeamViewer and SplashTop. These applications make use of data encryption to protect all data transmissions so you can rest assured your remote sessions are secured.
Advantages of using remote unattended access software
Remote access is not just for businesses that require remote IT support. The ability to access a computer remotely at any time bypasses traditional hurdles like physical location and even time zones. Unattended remote access allows all business processes to be performed securely and remotely. A healthcare provider can for example maintain and access patient records remotely across multiple practice locations. This approach ensures flexibility and convenience for both the patients and the providers.
There are a number of other benefits that can be enjoyed by using remote unattended access software:
1. Work from home without sacrificing efficiency or security
Working from home is no longer the exception to the work model. With recent global developments, more and more people are working remotely. With secure remote options, employees are able to access the network or any data or the remote servers on demand. In return, employees can easily receive remote support, and with the unattended option available – less downtime is experienced as users don’t have to be disrupted during work hours to allow IT to log in and investigate.
2. Supporting kiosks and IoT devices where no user is present
In the world of the Internet of Things (IoTs), the ability to remotely access smart devices for fault finding, security patches, or software upgrades is priceless. A simple example – imagine a casino group that owns 100s of slot machines over many physical locations – the ability to remotely access these machines while they are unattended for firmware or software updates is immutable.
3. Ensure education doesn’t take a back seat
Remote learning is facilitated when learners can access often expensive specialized software (such as 3D modeling or video editing applications) from a remote server at any time. Additionally, integrating user-friendly online video makers into the virtual learning environment can enhance creativity and multimedia skills, providing students with accessible tools to express their ideas through engaging visual content.
4. IT support made easier and more efficient for your team and customers alike
Tech support can be performed more effectively using unattended remote access software. Maintenance tasks like software updates, security patches or support can happen at any time and even after hours thus limiting any downtime and loss in productivity.
5. Enhances remote healthcare services
With the increased popularity of telemedicine, the healthcare industry can benefit from unattended remote access by allowing patients and practitioners access to patient files ro anywhere and at any time that is convenient – while remaining HIPAA-compliant. Various medical apparatus can be accessed and operated remotely and during all hours thereby increasing the return of investment on expensive equipment.
6. More freedom to professionals in the financial industry
Professionals in all industries can rest assured that they can work remotely and securely. Financial companies can rely on encryption and two-factor authentication implemented by unattended remote access software to secure their data during remote sessions.
7. Protect and empower retail brands
With the ever growing popularity of online shopping, retailers have become growing targets for hacking and data theft. Point of sale devices need to be secured, and with their remote nature, the ability to access them unattended is an invaluable tool for business.
Unattended remote access software makes it possible for retailers to provide a PCI DSS (Payment Card Industry Data Security Standard) compliant solution for their customers, without sacrificing any performance in speed.
Drawbacks of unattended access
While there are many obvious benefits using unattended remote access software, there are also a few of disadvantages that should be considered:
Connectivity
Remote access whether attended or not requires internet connectivity. Without a reliable and fast connection, any actions taking place remotely are dependent on your network speed and performance.
Privacy
In the online world, privacy is a very important factor. The idea of allowing someone access to your computer unsupervised can sound crazy. It is important that all staff members making use of these tools abide by the company privacy policy, and all employees should be vetted and trained accordingly. Any compromises to security is not just bad from a personal user point of view, but a data breach that affects the entire company is not just costly but can be detrimental.
The differences between attended and unattended remote support
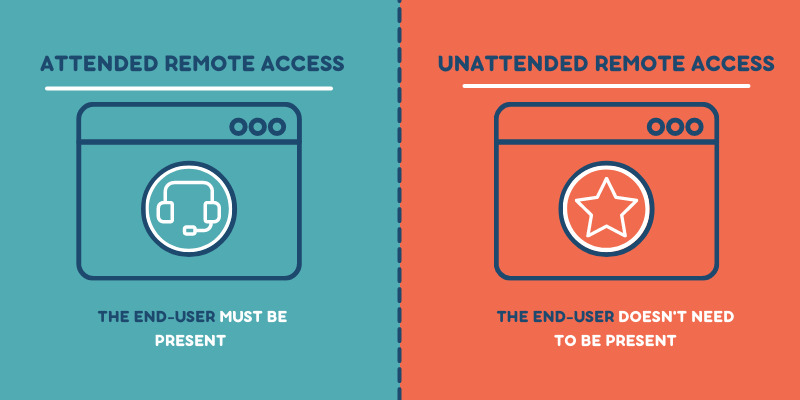
To attend or not to attend, the decision to use unattended remote support depends on your business model. If your company spans many physical locations and time zones or you need to provide support 24/7 – making use of unattended remote access makes sense.
The differences between attended and unattended are documented in the table below.
Attended | Unattended | |
Access to any remote computer or device. No additional installation required. | WHAT | Access a remote computer at any time without the need for anyone at the remote computer to approve. |
A remote computer is accessed while the user is logged in and in attendance during the remote session.
| HOW | In order to use unattended remote access, a lightweight agent needs to be installed on both devices. With the remote agent activated, an authorized user can access that remote device at any time from anywhere. |
• Improved productivity; | WHY | • Lower operating costs; |
• IT support / help desks; | WHO | • Managed Service Providers (MSPs); |
There are a number of free and paid software solutions available should you decide to make use of unattended remote access. We made a complete review of remote access software for you.