How to secure remote access to corporate network
The COVID-19 pandemic has been responsible for extensive changes across all facets of society. People have had to adjust to a new way of living as they attempt to keep themselves safe and curb the spread of the disease.
A direct response from the business world is the increase in the number of employees working remotely. This increase has made it vitally important for companies to provide secure remote access to their internal networks to ensure a seamless and uninterrupted working process, while keeping all corporate resources safe.
The importance of secure remote access
A remote workforce presents new and diverse cybersecurity threats that need to be addressed to protect sensitive data and business resources. Difficult challenges need to be solved to provide robust remote access security. The following obstacles complicate the implementation of a remote access security system.
Reasons why companies need to protect their network during remote access
✦ Remote workers need to use a public Internet connection to communicate with corporate systems. Unauthorized actors with access to unprotected transfer protocols can steal valuable and sensitive data.
✦ Remote workers and their machines may be more prone to phishing attacks than individuals working in a traditional office. This is especially true if they are using personal devices or computers that may not be adequately secured. Employees may share the device with other family members or use it for personal use and inadvertently click on a phishing lure that would not make it through corporate firewalls or email scanning applications.
✦ A new set of tools is required by remote workers to replicate the functionality of being in the office. This brings up more remote access security issues, as each application expands the surface for cyberattacks and may introduce new vulnerabilities.
Organizations moving away from the centralized office model need to make sure that remote access connections are secure. Inability to provide the required level of security is an invitation for hackers to invade a company’s systems with malicious intent such as launching malware or initiating a data breach.
Before organizations can determine how to secure remote access, they need to understand the potential risks to the business. Following are some of the most common remote access security issues companies have to address.
Main issues that businesses need to address with remote access for their employees
✦ Remote devices are a necessity for remote workers. In some cases, organizations are supplying their employees with the hardware they need to do their jobs. Other companies are opting to allow workers to use the bring your own device (BYOD) model. This complicates efforts by the IT team to manage the devices and users may object to some of the security software their company wants to install.
✦ Outdated or overly-permissive remote access policies and firewall rules pose a substantial threat to corporate data resources. Virtual private networks (VPNs) previously used by skilled and authorized technicians may now be open to the general remote worker population. A compromised VPN connection may enable intruders to access all network resources, not just those used by the victimized employee.
✦ Monitoring remote activity can be difficult and contributes to a lack of visibility by the network and security teams. Without adequate visibility into system activity, teams cannot perform activities like preventing malware attacks or detecting advanced threats.
✦ Inferior password practices such as reusing passwords or mixing home and business credentials can result in compromised personal and corporate systems.
How businesses are handling the challenge of secure remote access
Implementing a security system with remote access considerations presents substantial challenges to organizations and their employees. Companies should approach the task of improving remote access security methodically, as many moving parts need to work together to provide the level of security required by a remote workforce.
The chart from State of cybersecurity report 2020 by Wipro and Statista estimates illustrates how respondents to a global survey are prioritizing their actions to promote stronger cybersecurity after the emergence of COVID-19.
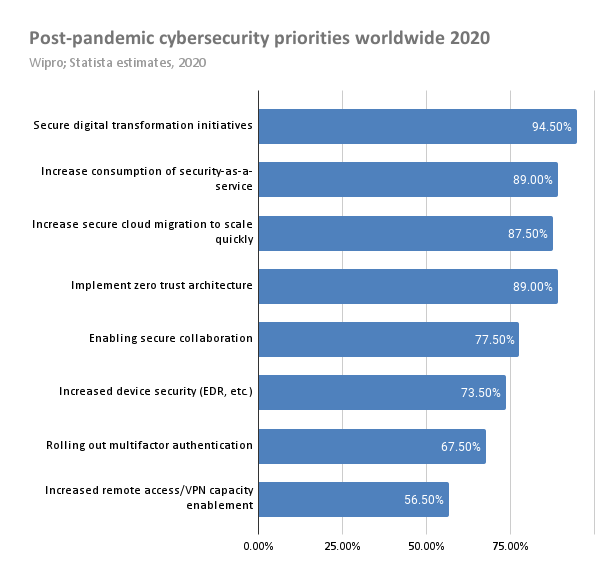
The majority of companies identify securing digital transformation initiatives as their top priority. This includes activities such as involving IT security personnel in all key business decisions and educating employees regarding cybersecurity risks. In many cases, a shift in corporate culture is necessary to accomplish an organization’s digital transformation.
Other priorities include increasing the use of security-as-a-service and other public cloud offerings to take advantage of innovative secure remote access solutions. The cloud is a very attractive option for smaller companies that may not have the necessary in-house security expertise required to deploy secure remote access.
Implementing the Zero Trust security model is also high on the list of priorities. This model offers one of the best methods of remote access security by eliminating employee access to resources they don’t need for their jobs. We will look more closely at Zero Trust later in this article.
The use of remote support tools is crucial for solving this problem successfully. Organizations can improve their general security stance, protect against unwanted access, and guarantee safe and effective management of remote access in professional environments by incorporating remote support software as a key element of their security approach.
Businesses can use remote access software like HelpWire to improve and safeguard communication between remote users and remote staff while creating secure connections with remote systems.
HelpWire’s goal is to give our users and their clients the safest remote desktop assistance experience. We use an industry-trusted validation system, encrypt all sessions with 256-bit AES and corporate-level TLS, and use AWS data centers to host cloud infrastructure.
The next chart we would like to draw your attention to displays the percentage for organizations that have specific cybersecurity rules or controls already in place. The survey has been held by Ipsos MORI and Institute of Criminal Justice Studies in UK, and called Cyber Security Breaches Survey 2021. The table lists businesses and charities separately, and in all but a few instances, business use of these items exceeds that of charitable organizations. We will concentrate on how businesses are implementing these rules and controls.
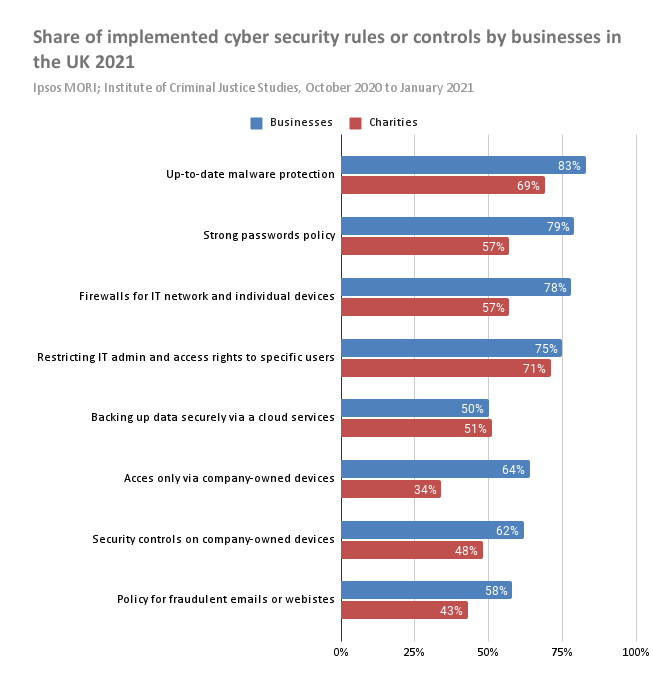
Updating malware protection is deemed very important by respondents, with over 80% of businesses undertaking this task. The increased prevalence of ransomware makes keeping malware out of internal systems a high priority for all organizations.
Strong password policies are being implemented by 79% of businesses. Weak and default passwords are responsible for many remote access security issues. Forcing employees to use strong passwords and change them regularly strengthens security and promotes secure remote access.
Other measures being taken by a majority of business respondents include implementing network-wide firewalls that also address individual devices. Many businesses are restricting administrator-level credentials to a controlled group of employees, and only allowing access through company-owned devices.
Providing secure remote access for BYOD employees
Businesses that allow employees to follow the bring your own device (BYOD) model have additional remote access security issues not faced by companies using corporate-owned equipment. The following techniques can be used to minimize the risks associated with BYOD employees.
✦ Always connect through a VPN. Reliable authentication is necessary to prevent stolen passwords from enabling hackers to compromise the whole network from a single mobile device.
✦ Using Microsoft’s Remote Desktop Protocol (RDP) provides connectivity to specific machines or resources rather than the network as a whole. The protocol is available in a variety of tools for most major computing platforms.
✦ Cloud computing solutions are built with secure remote access in mind. All interactions with the cloud are remote, so there is no need to add on additional solutions to provide remote access security.
Taking these steps, combined with educating employees on the use and misuse of BYOD devices, will minimize remote access security issues.
The benefits of the Zero Trust security model
The Zero Trust security model requires all internal or external users to continuously be authenticated, authorized, and validated before gaining access to resources such as applications and data. The following three main principles apply to the Zero Trust model.
Main concepts of Zero Trust architecture
✦ Verify explicitly by authenticating and authorizing access requests based on all available data points.
✦ Use least privileged access to limit user access with just-in-time and just-enough-access which protects data and promotes productivity.
✦ Always assume a breach to intensify security measures such as encryption and encourage threat detection.
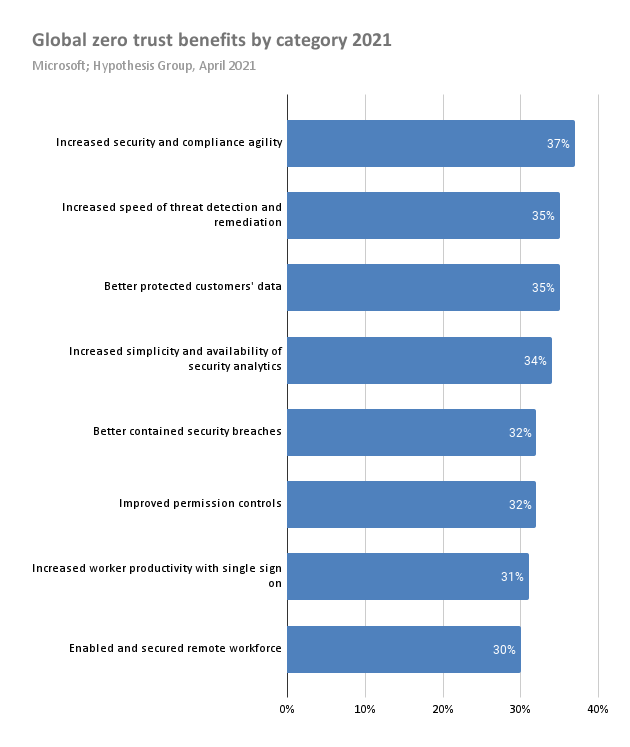
As evidenced in the following chart based on Zero trust adoption report (page 15), by Hypothesis Group, organizations are better able to protect customer data, increase security and compliance agility, and improve identification and remediation of security threats when employing the Zero Trust model.
Conclusion
Whatever direction the COVID-19 pandemic takes, it’s a safe bet that remote work in some form is here to stay. Companies can take advantage of things like reducing employee commuting time and allowing for better work/life balance to develop a more satisfied and motivated workforce. The challenge is for organizations to figure out how to secure remote access to align with their business objectives.
Remote employees increase the potential attack surface an organization must defend from cyberattacks. Companies need to address the complexities of BYOD employees and the risks they bring to the business. In some cases, such as in highly regulated industries, it may be necessary to only allow access to corporate resources using company-owned devices.
It is not a trivial matter to implement secure remote access but it can be done effectively with the right mindset, tools, and policies. Companies need to evaluate their current position regarding remote access and make the necessary changes to keep things running smoothly in the post-COVID era. Failure to modify practices to enable employees to securely access company systems remotely will leave businesses at a competitive disadvantage from which they may not be able to recover.