Technical Support Scams on Mac, Windows or Android: How to Get Rid of Them?
Virtually everyone who uses a computer has been approached at one time or another by a tech support scammer. This article will look at some of the most common types of tech support scam on Mac, Windows or Android and best practices that will help you avoid becoming a victim. We will also discuss what you should do if you get scammed and why you should take the time to report the incident.
How a Computer Technical Support Scam Works
As seen in the accompanying graphic, there is a wide variety in the types of scams perpetrated and the types of individuals most likely to be targeted. The collected data also shows that consumers are extremely wary of unsolicited tech support calls, as they should be.
The graphics also identify the four major types of U.S. tech support scams. Let’s take a close look at each kind of computer tech help scam so you can be prepared and avoid becoming an unwitting victim.
Phone calls
Scammers will often give unsuspecting victims a phone call and pose as computer technicians from trusted tech companies claiming that your device has a virus and needs fixing. This, of course, is part of the scam where they will ask you to give them remote access to your computer so that they can “help” you get rid of the virus. After the whole process, you will be asked to give them a sum of money for payment by wiring them or sending them gift cards.
It’s always best to just hang up and ignore calls that you’re not expecting because often than not, they’re just scam calls.
Fake tech support popup warnings
Other scammers take advantage of some people’s gullibility and lack of tech knowledge with the use of fake pop-up alerts. These pop-ups appear on your browser while you browse the Internet. They try to warn you of viruses that may have infiltrated your system. Often, they’ll be using names of trusted companies such as Microsoft so that people will not doubt their credibility and willingly give them a call.
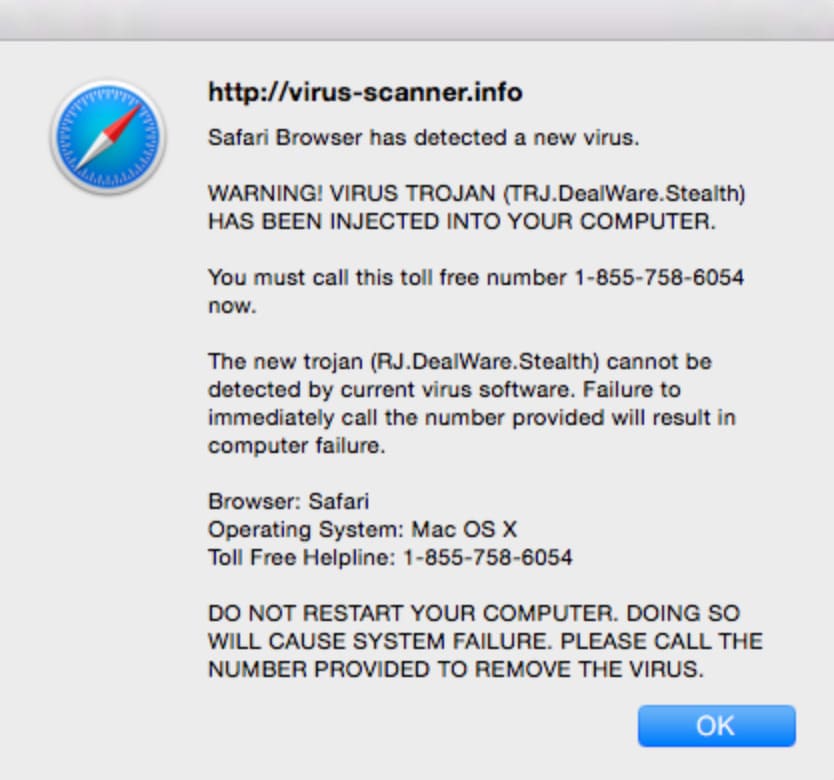
If you ever encounter these types of pop-ups, avoid calling the attached phone numbers. Instead, you may have to restart your web browser or reboot your system to remove this offending popup from the screen.
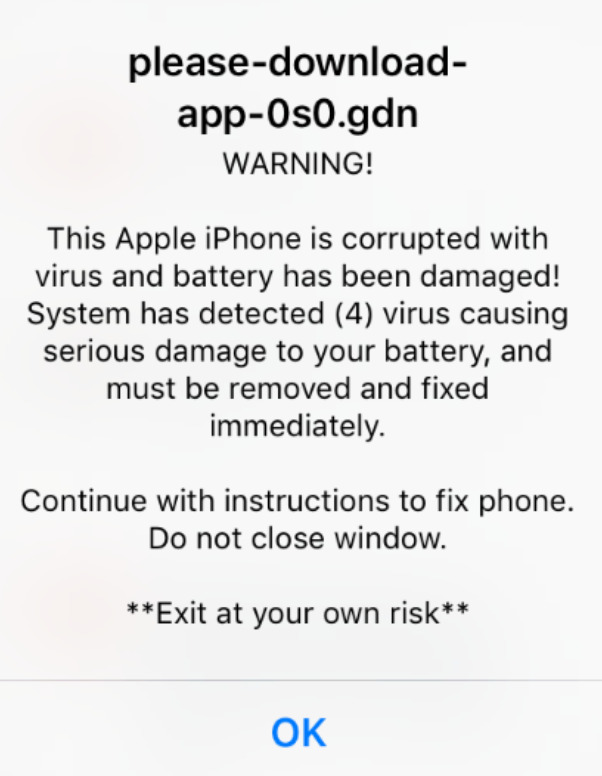
Similar to fake tech support popups, unsolicited emails purporting to be from a tech support company may ask you to click on a link or provide a list of phone numbers for you to call. When you call the tech support number, a representative will try to obtain some type of information from you or request remote access to your system.
A good rule to follow is to never click on unverified links from technical support teams or any other type of organization. These links may install malware on your machine and allow scammers to get at your sensitive and personal information.
Online ads and search results
In a slightly different approach to perpetrating a tech support scam, some nefarious hackers post ads that are returned in standard Internet searches. What may seem at first glance to be a legitimate company may only be a front for hackers intent on stealing your data.
The best protection against this kind of tech support scam is to only engage with organizations that you trust. While this can be difficult at times, taking a chance on an unknown support site can set you up to be a victim.
Actions to Take if You Were Scammed
You should take several steps if you suspect or are certain you have been victimized by a tech support scam pop up.
Scan your computer for malware or viruses
Run a reliable anti-malware tool to determine if your machine has been infected. You can use some of the most popular and trusted anti-virus software there are today including HitmanPro, Malwarebytes, and AdwCleaner. These are software you can use to remove any type of virus in your system that is often undetectable by other software. Remove any suspicious software from your computer and delete it from your Trash or Recycle bin.
- Removal instructions for Mac
- Remove tech support scam on Windows
- Remove tech support scam pop-ups on Chrome
- Remove tech support scam pop-ups on Safari
- Deal with tech support scams in Firefox
- Remove tech support scam on Android
Removal instructions for Mac
Option 1: delete suspicious profiles on your Mac
One strategy that these fake tech support individuals use to succeed in their scams is by creating their own configuration profiles on your Mac. They do this to prevent you from deleting the malicious software they have just installed on your device to gain control of it. This will also prevent you from changing your browser’s settings.
To see if there are any suspicious configuration profiles on your Mac that you don’t know about, the following steps should be followed:
- Open Profiles list. Open the Apple Menu, click System Preferences and select the profiles icon.
- Remove suspicious profiles. After opening the Profiles list from your System Preferences, search for any suspicious profiles and click the minus sign alongside it. Then, select Remove to delete the profile.
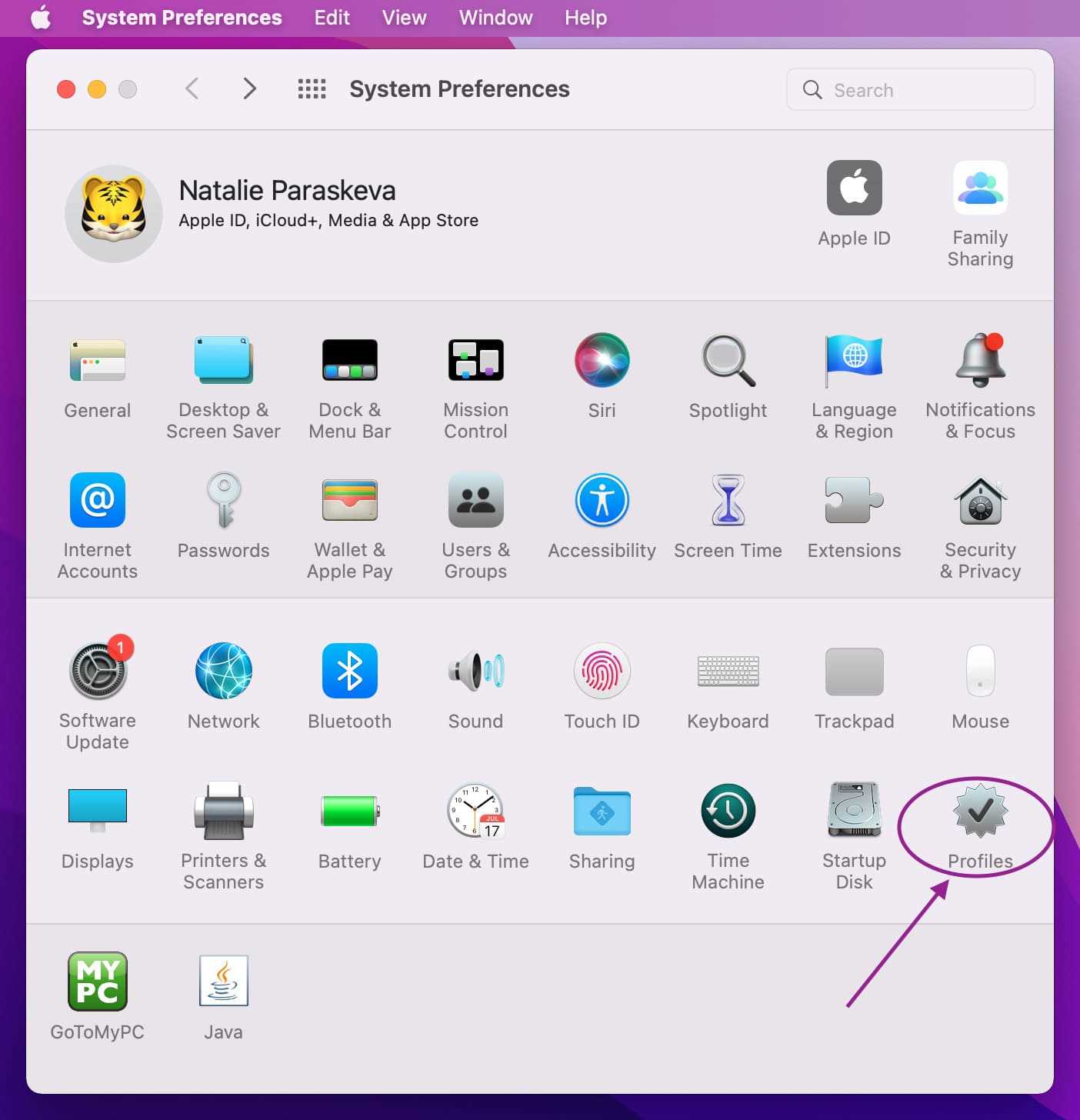
If you were not able to locate a profiles icon in the System Preferences window, this means that there are no profiles created on your device.
Option 2: Uninstall malicious apps that are causing the pop-ups from your device
If there were apps installed on your device without your permission, you could try to identify them and remove them to get rid of the unwanted scam pop-ups on your device.
- Close any suspicious apps opened on the Apple menu bar. On the top right corner of your screen, in the menu bar, if you find any apps that you don’t recognize or remember opening/installing, Close them.
- Open the Applications folder. Go to your Finder and select the Applications icon.
- Delete malicious applications. After clicking the Applications icon, a window will appear showing a list of applications on your device. After spotting the malicious applications, right click on them and select “Move to Trash.”
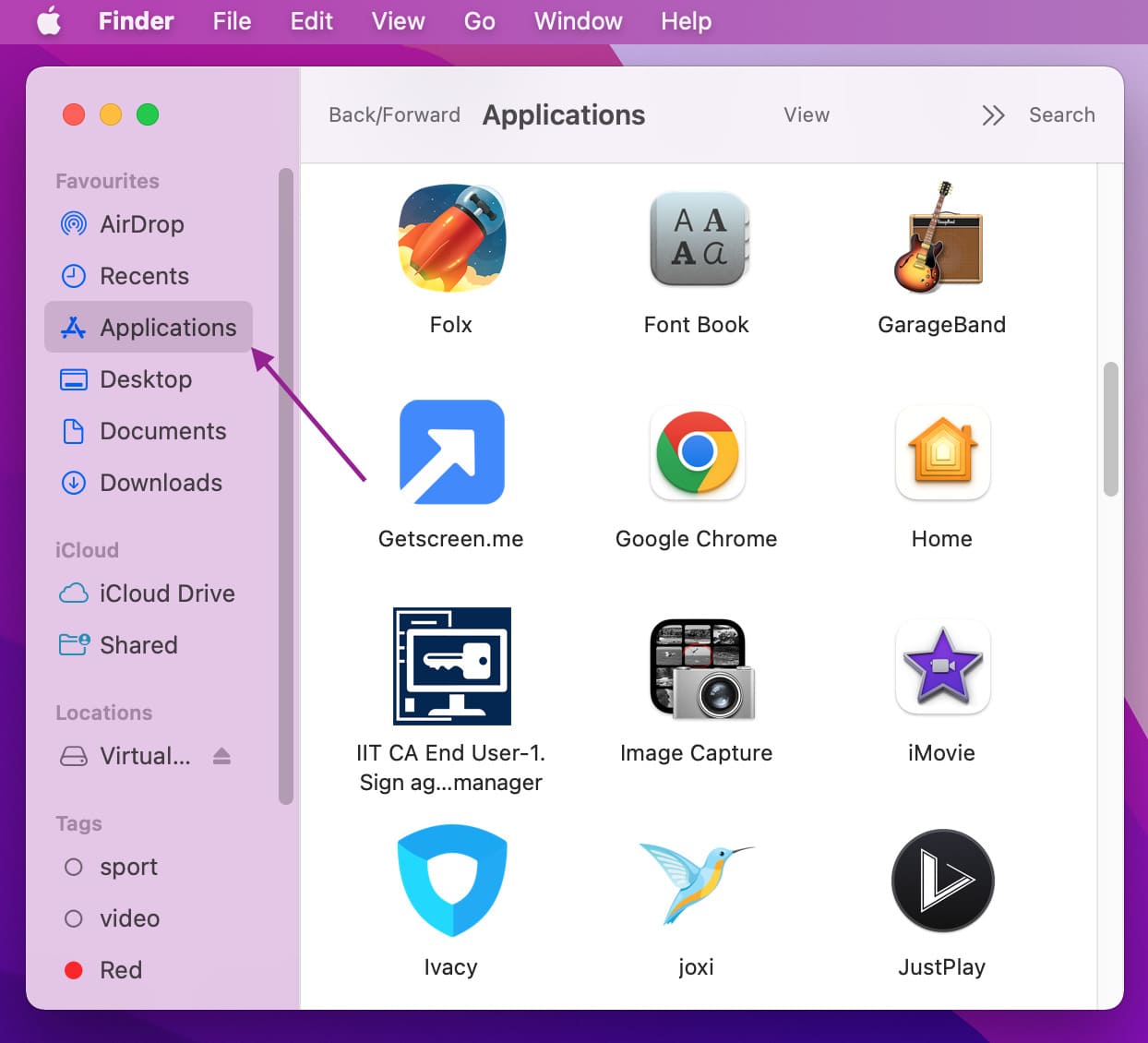
Remember, if the scammers have successfully installed a remote support program on your device, you’ll need to uninstall it. You can do this by searching for them in your Applications list by following the steps above. Remote support programs include TeamViewer, LogMeIn, ScreenConnect, AnyDesk and GoToAssist, among many others.
It’s also best to be wary of apps on your device that you don’t remember installing or using at all. Some examples of malicious programs that you should be aware of include: FeedBack, Take Fresh, TopResults, SearchMine, PowerLog, MessengerNow, ImagePrime, GeneralNetSearch, Reading Cursors, GeneralOpen, PDFOnline-express, WebDiscover, See Scenic Elf, MatchKnowledge, Easy Speedtest and many more.
Option 3: Delete malicious files
- Search for the following file paths, Open your Finder and click “Go to folder.”
– /Library/LaunchAgents
– ~/Library/LaunchAgents
– /Library/Application Support
– /Library/LaunchDaemons
- As you browse through the following file paths, make sure to look around for any suspicious applications lurking in your files. If you don’t remember installing the files or they don’t seem like anything that your Mac is using, delete them, some files that you should delete include “com.adobe.fpsaud.plist,” “Installmac.AppRemoval.plist,” “myppes.download.plist,” “mykotlerino.ltvbit.plist,” and “com.myppes.net-preferences.plist.” After locating the following files or other malicious files, relocate them to your Trash folder.
How to remove Windows tech support scam on your Windows computer
There are a few steps you can take if you think that a scammer has gained access to your information.
You can uninstall the applications that you were asked to install on your device:
- Open Windows Settings. You can do this by pressing the “Windows + I” shortcut on your keyboard or by manually opening Settings from the Start menu.
- Open the “Apps and Features” window. Click on “Apps” on the left sidebar of the Settings window.
- Uninstall suspicious programs. Scroll through the app list and locate any malicious apps that may have been installed without your permission. If you find any, click the three-dot menu alongside it and choose the “Uninstall” option.
- A pop-up box will appear. Select Uninstall and proceed with the necessary steps to remove the program from your system.
Beware of some applications that may try to confuse you with their misleading prompts while you go through the uninstallation process.
Scan Windows with your built-in Windows Security to get rid of Microsoft scam pop ups
- Open your Windows Security app. Next, go to Start > Settings > Update and Security and select Windows Security.
- In the Windows Security App, select Virus and Threat Protection.
- Begin scanning. Open the “Current Threats” tab and select Scan Options. Then, open Threat History to Run a new advanced scan.
- After selecting Run a new advanced scan, you will be asked to choose from the following scan options:
a. Full Scan – scan all existing files in your system
b. Custom Scan – choose which location in your system to scan
c. Microsoft Defender Offline Scan – reboots your system and performs an offline scan before start up to get rid of sneaky Microsoft scams malware. - Click Scan after selecting your desired scan option.
It is vital to keep your security programs updated all the time. To make sure that you don’t miss any updates every now and then, visit your Windows Update settings to scan for available updates.
It is also smart to regularly change your passwords to prevent easy infiltration.
How to remove tech support scam pop-ups on your Chrome browser
You can reset your browser to its default settings to erase irregularities such as malicious extensions, unauthorized search engines and unwanted notifications.
- Open your Chrome Settings. On the top right corner of your Chrome browser, click on the three-dot menu. Select Settings.
- Open the Advanced Settings tab. After clicking on Settings, you’ll be able to spot the Advanced Settings option on the bottom part of your browser or on the left-hand side menu, depending on your configurations and browser version.
- Click on Reset settings to their original defaults. You should be able to find this option in the Advanced Settings tab.
- Click the Reset Settings button on the confirmation dialog box that appears after you click on the Reset button.
Remove the unwanted policies created by malware from Chrome.
If resetting your Chrome browser’s settings still didn’t fix your issues, you can try editing Chrome’s unwanted policies. It is possible that a malicious program has created the unwanted policies on your browser that are giving access to scam popups and unwanted notifications. To ensure that there aren’t any unwanted policies on your browser, you can open “chrome://policy” by entering the URL in the search bar.
You can reset unwanted policies by following the steps below:
- Open a Terminal Window. In your Finder, locate Go > Utilities and select Terminal.
- Once the terminal window is open, input the following commands:
a. Defaults write com.google.Chrome HomepageIsNewTabPage -bool false
b. Defaults write com.google.Chrome NewTabPageLocation – string “https://www.google.com/”
c. Defaults write com.google.Chrome HomepageLocation -string “https://www.google.com/”
d. Defaults delete com.google.Chrome
DefaultSearchProviderSearchURL
e. Defaults delete com.google.Chrome
DefaultsSearchProviderNewTabURL
f. Defaults delete com.google.Chrome DefaultSearchProviderName
g. Defaults delete com.google.Chrome ExtensionInstallSources - Check if the policies have been removed from your browser. Search for “chrome://policy” on your browser and see if the same malicious policies still exist.
- Change your browser’s settings to your preferences if the policies have been successfully deleted.
Remove the “Managed by your organization” policy from Chrome
There are malicious programs out there that have the ability to set managed preferences on your Chrome browser. To check for these, you can follow the steps below:
- Close Chrome.
- Go to your Managed Preferences folder. First, open your Finder, search for Go, then choose Go to Folder. Next, type the location “/Library/Managed Preferences.”
- A window will open wherein you can search for the following files:
a. com.google.Chrome.plist
b. ]YourUsername]/com.google.Chrome.plst
c. [YourUsername/complete.plist
Once you’ve located the above files, you can check if they are legitimate files or not by opening them with TextEdit. If you find the URL of the troublesite in the text file, delete them and restart Chrome.
Delete Google Chrome
If the problem still persists even after following the above steps, it might be time to delete your browser. Removing your browser and reinstalling it may get rid of the unwanted tech support scam pop-ups. All you’ll have to do is locate the following files with your Finder and delete them.
Before proceeding, make sure that you don’t have any important data to save from your browser, like important bookmarks. Deleting the following items will delete all your browser data.
- – /Applications/Chrome.app
- – /Library/Application Support/Google/
- – /Library/Google/
- – ~/Library/Application Support/Google/
- – ~/LIbrary/Google/
- – ~/Library/Preferences/com.google.Chrome.plist
Restart your computer after deleting all the files. Then, download and reinstall Chrome.
Remove Safari tech support scam pop ups on your Safari browser for Mac
There are some easy steps that you can follow to get rid of popup messages on your Safari Browser.
- If a pop-up has an option to “Don’t show more alerts from this webpage,” select it, then click on the Confirm/Leave Page/OK button.
- When this option is not available, try clicking the Leave Page/OK immediately. If this doesn’t work, try pressing the Enter key.
Performing these steps may help you prevent the scam script from further preventing you from exiting the malicious page. If this method does not work, proceed with the steps below:
- Close the Safari browser. If you cannot access the close button or you cannot close the browser normally, Force Quit the browser.
a. Go to Apple Menu and choose Force Quit
b. You can also use the shortcut ⌘ (Command Key) + Option Key + Escape Key.
c. The Force Quit Applications window will appear, showing a list of apps running that you can close.
d. Force Quit Safari. Select Safari from the list of apps, then click on the Force Quit button.
e. A dialogue box will appear asking for your confirmation. Click Force Quit. - Open Safari while holding the Shift button to prevent previously closed tabs from opening again.
If you’re still experiencing the same problems:
- Force Quit Safari again following the above steps.
- Disconnect from the Internet. On your Mac’s menu bar, turn the Wi-Fi off or unplug the ethernet cable.
- Open Safari while holding the shift button to keep previously closed pages from loading again.
- Open Privacy Settings and select Remove All Website Data, then select Remove Now.
- Exit the Preferences window.
- Clear your browser’s history. Open the History tab and select Clear History. This is an optional step where you can delete your browsing history from a chosen timeframe to make sure that you don’t end up opening the same malicious web page again.
- Connect to the Internet. Turn on your Wi-Fi or plug in the ethernet cable.
When dealing with malicious cyberattacks such as these invasive scam webpages, it is a must to take utmost caution. Below is a list of recommended actions you can take in order to keep your Safari browsing experience free from these scams.
- Uninstall unfamiliar extensions. Go to your Safari’s Preferences menu and select Extensions. From there, look for extensions that you don’t use or don’t remember installing and uninstall them.
- Review your Website tracking settings. Go to Safari’s Privacy settings and check if your Website tracking settings are configured to your preferences.
a. For macOS Versions older than High Sierra, you can check if your Cookies and Website Data are set to how you want them. If you are unsure of how they should be set, you can simply choose Allow from websites I visit.
b. If your macOS Version is older than Yosemite, you will be able to choose to Block cookies and other website data from a list of sources, including third parties and advertisers. - Manage your data. Select the Manage Website Data button. Then, you can choose to delete all website data or select which type of data you want to erase, may it be your login credentials, cookies, autofill data, browsing history and whatnot. You can choose to Remove All data, but you will need to log back in on websites that require your login credentials.
Dealing with tech support scams in Firefox
Now, if you’re using Firefox for your Mac or Windows and you’re being bombarded by pop-up scams, spam notifications, malicious extensions and unwanted search engines, you can try resetting your browser settings to default.
Resetting your browser’s settings can fix a lot of issues, including the issues mentioned above, while still retaining important data like bookmarks, saved passwords, autofill information, and browsing history, among others.
First, search for 'about:support' on your browser’s search bar and head to the Troubleshooting Information page. Then, click Refresh Firefox to reset your browser’s settings to default.
- Go to Firefox’s help menu. First, click on the main menu button on the top right corner of your browser and select Help.
- Click on More Troubleshooting Information. If you are unable to access your Help menu for any reason at all, you can access this information by entering “about:support” in your search bar.
- Once the support information page is open, click on Refresh Firefox.
- A confirmation pop-up will appear. Click on Refresh Firefox.
- After your Firefox browser has reverted back to its default settings, a pop-up window will appear, showing you the summary of information that has been imported. Click Finish.
How to remove tech support scam on Android
Even when using your Android device, you aren’t going to be safe from support scams. The first step in getting rid of these malicious activities on your device is to check if any malicious apps have been installed on your device. Just remember that some pop-up scams have the capability to uninstall these apps on their own.
- Go to your device Settings. You can access this from your device’s main menu.
- Go to your App Manager. In the App Manager, you will be able to see a list of apps operating on your phone.
- Scroll through the list of apps and look for malicious or unfamiliar names in the list.
- Uninstall the malicious applications. Click on the application and select Uninstall. If the application is running in the background, Force Quit the application and Uninstall it.
Also, be aware of “legitimate” applications such as photo editing software, weather and camera apps that try to look like the genuine programs but are in fact just wise disguises for malware. Some of these clever malicious apps include: ES File Explorer, Z Camera, Amber Weather Widget, GO Weather Forecast and Widgets, Touchpal, and Kitty Play.
How to Delete a Suspicious App on Your iOS Device
Delete a malicious app entirely together with its configuration profile by following the steps below:
- Uninstall the application. While on your main menu, press and hold the application widget until the X icon appears in its top right corner. Click the X icon to delete the app.
- A confirmation pop-up will appear. Press Confirm.
- Delete the App’s configuration profile. Go to your Settings > General, then select Profiles and Device Management. Choose the app’s configuration profile and select Delete Profile.
- Restart your iOS device. This works on iPhone, iPad or iPod devices.
Report tech support scams
You should take the time to engage in a little computer scam reporting if you accidentally gave a scammer remote access to your computer. The lessons learned from your experience can help others avoid the same fate and may lead to the apprehension of the rogue hackers behind the scam.
There are several ways to file tech support scam reports. The Federal Trade Commission has a site dedicated to reporting fraud that can be used to document tech support scams. You can also contact the FBI and other consumer protection agencies with information regarding the scam.
You can also report any unsafe website that you suspect is a phishing website or contains malicious content directly to Microsoft by filling out a Report an unsafe site form or using built in web browser functionality.
Windows:
Help Microsoft deal with these scammers by immediately reporting an encounter with them at www.microsoft.com/reportascam.
Apple:
If you are a victim of phishing scams by individuals posing as Apple, may it be through emails, browser notifications or pop-ups, report the incident to reportphishing@apple.com.
How to Keep From Getting Scammed
It can be challenging to avoid advanced tech support scams. As consumers become more knowledgeable about the scammers’ methods, tenacious criminals keep looking for new ways to get past their defenses. Following are some tips and best practices to steer clear of tech support scams.
- • Don’t click links in suspicious or unsolicited emails or popups. If you think the link is a legitimate request to verify an account or conduct other types of personal business, don’t use the embedded link. Instead, log into the account through your web browser and perform the activity without involving the email or popup.
- • Only provide secure remote access to your computer to trusted individuals. Computer technician scams rely on the scammers’ ability to trick unsuspecting users into giving up credentials. Unless you have initiated contact with a technical support team and are certain of their identity, don’t let them into your computer.
- • Understanding how an authentic technical support team operates can help you avoid having to say “I gave a scammer remote access to my computer!” A reputable company will never call you and ask for access to your computer unless you have initiated the activity. They will also never instruct you to call a number as the result of a popup.
- • Keep your antivirus software running and updated with the latest virus databases. Infection with a virus or malware can compromise your credentials, expose sensitive data to theft, and allow scammers to access your machine. Updated antivirus tools are one of the best methods of protection.
Following these best practices can help you avoid getting caught in a tech support scam. There’s nothing wrong with being exceptionally cautious regarding providing access to your computer and its valuable information. You need to constantly be on the lookout for these scams, as cybercriminals are always looking for a new victim. Don’t fall for their tricks and stay safe!