Uncovering Security Issues in Microsoft Teams
A part of Microsoft 365, Microsoft Teams is arguably one of the most popular communication platforms in the world. It has seen a significant increase in daily users in the past few years, accumulating millions of new users in 2021 and 2022.
The platform offers a variety of collaboration tools, including business messaging, video meetings, calling, and file sharing, to name a few. However, while these features are helpful, their worldwide use resulted in MS Teams vulnerability.
In this post, we will discuss the most common Microsoft Teams security risks and the measures their security experts take to solve them. We will also take a look at other threats and what users can do to address them.
Most Common Microsoft Teams Security Issues and Ways to Fix Them
Compromised-key attack
A compromised-key attack is one of Microsoft Teams security concerns. It pertains to a situation wherein a perpetrator steals a private key, which is a code or number, to access a secured transmission and decrypt encrypted information. To avoid this from happening, Microsoft Teams safeguards the key data for encryption for the Transport Layer Security (TLS) connections using the Public Key Infrastructure (PKI) features incorporated in the Windows Server operating system.
Denial-of-service attack
This kind of cyber-attack takes place when an attacker disrupts services to prevent the network from working normally, making the network resource inaccessible to users.
To combat the attack, Microsoft Teams runs Azure DDoS network protection and controls client entreaties from similar endpoints, subnetworks, and federated entities.
Eavesdropping attack
Also called snooping or sniffing, Eavesdropping is another one of Microsoft Teams’ security issues. As the name suggests, eavesdropping occurs when a perpetrator secretly listens to communications between users to obtain private details, including node identification digits, application-sensitive information, and routing updates.
To prevent this kind of cyber attack, Microsoft Teams utilizes mutual TLS and Server to Server OAuth for server communications within Office 365 and Microsoft 365. Moreover, they use TLS from customers to the service. They even encrypt each traffic on the network and authenticate all parties.
IP address spoofing
Spoofing happens when an attacker discovers and employs an IP address of a device (like a computer), a network, or a network component without authorization. And as a result, the attacker can take control as if they are the entity the IP address usually identifies.
Teams diminishes this attack through their TLS, which encodes all traffic and validates all parties. Still, the attacker could identify the Domain Name System (DNS) server address. But since Teams has an authentication process with certificates, the attacker won’t be able to obtain valid information necessary for spoofing one of the parties in the communication.
Man-in-the-middle attack
This occurs when the attacker puts himself between two users in a conversation (or between a user and an application) to steal personal details, like login credentials, credit card numbers, and account information.
Teams prevents man-in-the-middle attacks on media traffic between two parties through the use of Secure Real-Time Transport Protocol (SRTP) to cipher the media stream. Between two parties, cryptographic keys are arranged over Teams Call Signaling protocol, which leverages TLS 1.2 and AES-256 (in GCM code) encrypted TCP or UDP channel.
Unauthorized devices
Unauthorized devices are one of the most common Microsoft Teams security risks that organizations face in their Teams environment. Data leaks are one of the potential results if these are not prevented.
But there’s a way to limit access to unauthorized devices to protect your organization while maintaining high workforce productivity. For instance, administrators can let users from unauthorized devices view documents but prohibit them from downloading or editing documents.
Screen sharing
Screen sharing is one of the crucial components of successful video conferencing, especially when the host or other attendants have to explain complex information. But it also falls under Microsoft Teams security concerns.
While this feature is convenient, it brings potential security and compliance risks to your organization. For example, when a user who’s sharing a screen fails to turn off their notifications beforehand, alerts from private channels may appear while screen sharing — resulting in an accidental leak of private details related to the user or the business.
File sharing
When working remotely, team members surely can’t give documents to each other physically. This is where file sharing comes in. But like screen-sharing, this ability can also cause various security concerns to users. The default sharing permissions in Teams will be the same as those set at the Tenant level since Microsoft Teams security settings are obtained from external applications, including OneDrive and SharePoint.
Microsoft 365 has a solution for this — Sensitivity Labels, which are access rules that you can configure and assign to documents, Microsoft Teams, and SharePoint platforms. Those rules allow users to control who can directly access a document or other files.
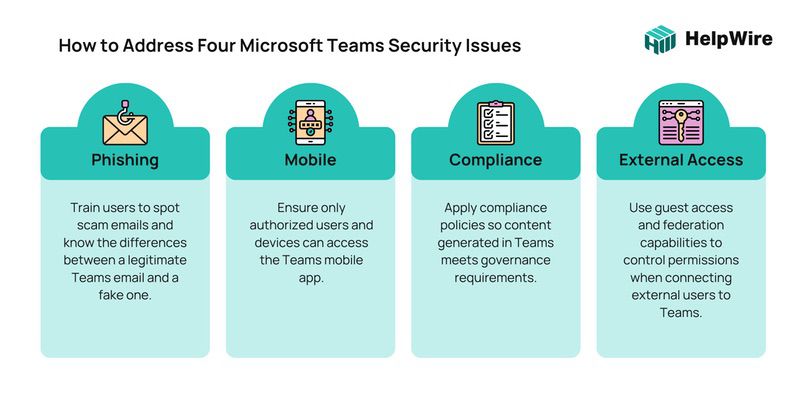
Compliance
There will be certain periods during which your organization must keep documents to maintain compliance with organizational regulations. The downside is that retaining documents even after this period can result in Microsoft Teams security risks, specifically data leaks. Therefore, it is best to dispose of such papers to prevent unwanted leaking from happening.
Phishing
Phishing is one of the cyber-attacks that has been happening for years, and attackers have been developing this tactic to coincide with how organizations operate today. In fact, malicious links abound in Microsoft Teams, and they take users to malicious sites or instigate a download of malware onto their computers or other devices.
Microsoft 365 addresses this issue with Safe Links, a feature that offers URL scanning before a user is led to the link’s address.
Guest users
Microsoft Teams security concerns also include guest users. With the sudden shift in remote work, the number of external contractors, vendors, and other guests being acquired to contribute to the organization has increased.
However, there are potential situations wherein you want to minimize guest access to certain mediums to safeguard important business-related information that guests don’t need to complete their tasks.
Administrators can simply turn on and off guest access to Teams in general. But note that granular control of guest access to certain channels will require you to create private mediums to which particular guests have no access.
Replay attack
A replay attack is a kind of cyber-attack that occurs when an attacker identifies a data transmission between two parties and would either repeat it or delay it for malicious purposes. Teams uses SRTP with a signaling protocol to handle this issue, allowing the receiver to sustain a list of RTP packets and compare new packets with those in the index.
Viruses and worms
Capping off our list of MS Teams security issues is the virus and worms. A virus refers to a malicious code that replicates itself and spreads from one device to another. It would need a host, like a program, a file, or an email, before it reproduces more similar codes.
A worm is a unit of code that self-replicates like a virus, but it differs in a way that it doesn’t need a host to work.
These two typically appear during file transfers between users or when URLs are sent from other clients. One of the scenarios that can happen if one of these two gets into your computer is that it will send messages to other people using your identity.
The best way to mitigate this issue is to periodically scan for viruses to ensure your computer is free of malware.
Microsoft Teams Vulnerability
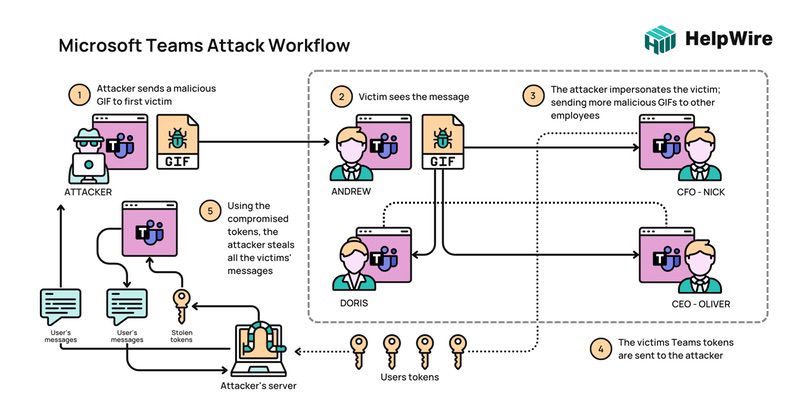
In 2022, leading cybersecurity company Vectra found a vulnerability in Microsoft Teams. Analysts from the agency claim that the Teams desktop app for Windows, Mac, and Linux saves authentication tokens of the users in plain text without access protection. This means that if an attacker hacks a system with Teams installed, they can easily snatch these tokens and use them to log into the accounts of users.
Vulnerability in Microsoft Teams derives from the app being an Electron operating in a browser window. Because Electron apps don’t include encryption support or secured file locations, using them is somewhat easier. However, the downside is that it is risky when it comes to data protection.
Vectra further explained that the tokens being stored were active and not “an accidental dump of a previous error.” The company added that those tokens gave them access to the Outlook and Skype APIs. The “cookies” folder also contained tokens, account details, session figures, and other essential information.
In response to Vectra’s discovery, Microsoft stated that the situation isn’t that alarming and that patching won’t be necessary. “The technique described does not meet our bar for immediate servicing as it requires an attacker to first gain access to a target network,” Microsoft said. They added that they would consider addressing the issue in a product release in the future.
However, Vectra begged to disagree and even created an exploit, which lets users message themselves, to prove Microsoft Teams’ vulnerability. The exploit obtained authentication tokens in the messages by viewing the cookies database via the SQLite engine.
The cybersecurity company then suggested using the browser version of the Teams client if you’re worried about your business tokens getting stolen. Also, Linux users are advised to switch to a different collaboration platform.
Microsoft Teams Reputation
As mentioned above, Microsoft Teams saw a striking rise in popularity during the COVID-19 outbreak. Because people were asked to stay home, collaboration tools were a great option to continue the productivity of temporary remote employees.
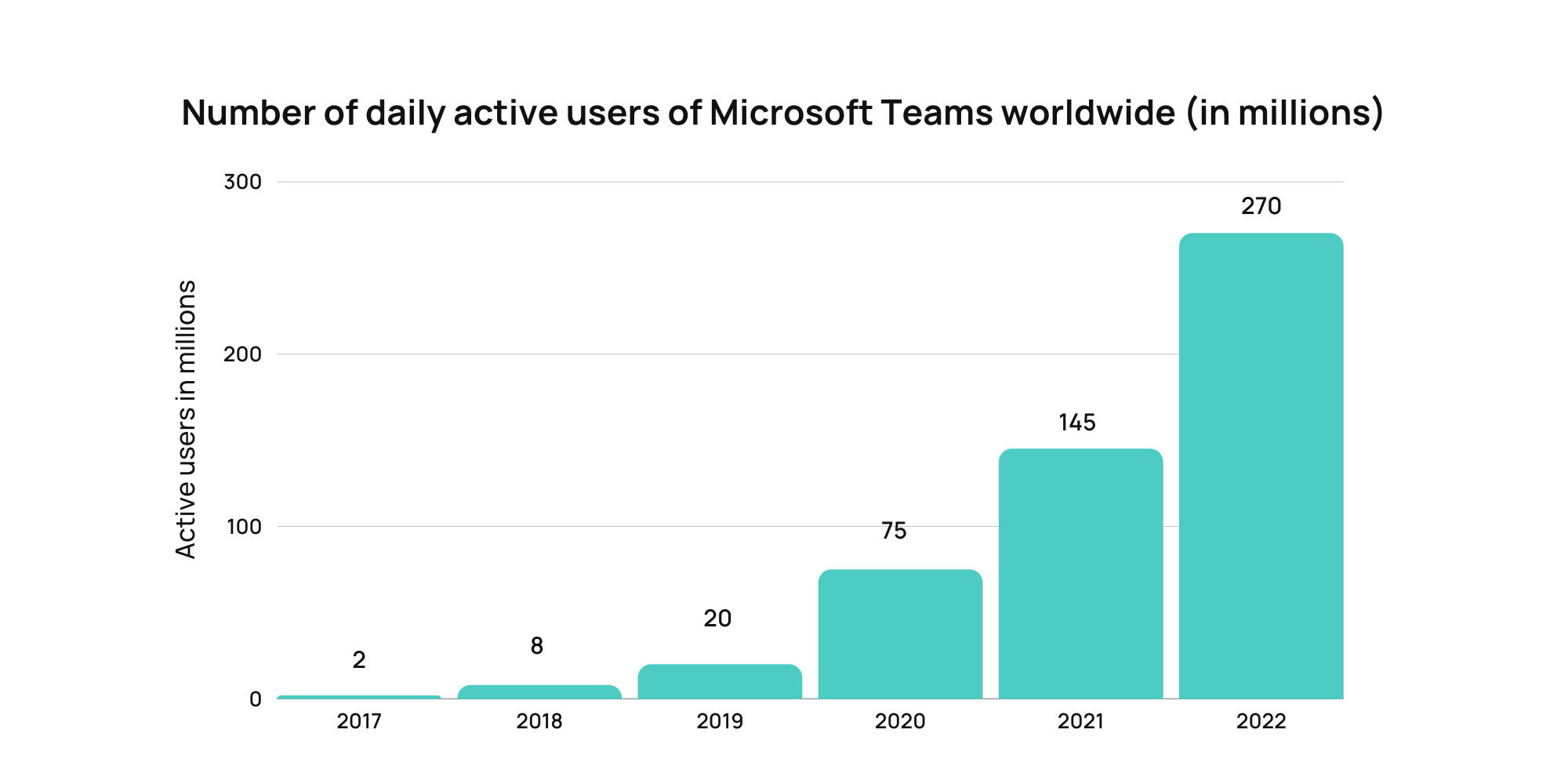
In particular, the platform recorded 145 million active daily users in 2021 and reached 270 million daily users in 2022 (see the chart below). In addition, based on the Gartner survey, there has been a 44% increase in workers’ utilization of collaboration tools since 2019.
While crucial for virtual work, collaboration apps can give rise to severe threats to organizational security and privacy without proper management. The thing is, collaboration apps are prone to vulnerabilities. Like any browser-based software, they contain hidden bugs and can be the object of cyber-attacks like phishing.
As such, organizations should strive to keep these fundamental tools secure and safe. There are ways to limit the risk of collaboration apps, including setting a strong password, executing content guidelines for platforms, using web application firewalls to determine layer attacks, and deploying cloud access security brokers to detect data exfiltration.
Conclusion
Microsoft Teams features a variety of tools organizations can use for remote and real-time communication and collaboration, meetings, file sharing, and more. It’s a one-stop shop for all your virtual business needs.
However, the dramatic increase in active users in the past few years brought about a corresponding rise in possible Microsoft Teams security risks. Hence, it’s crucial to secure the Microsoft Teams environment of your organization to make sure that your valuable data are secure while you continue making collaborative efforts that help your business grow further.
With sufficient knowledge of the most common Microsoft Teams security issues, you and your colleagues will be able to come up with solutions and prevent worse scenarios like data leaks from happening.