Is Splashtop Secure? A Well-Detailed Examination of Remote Desktop Software
In recent years, cybersecurity has become more analytical than before. Due to its user-friendly and extensive features, Splashtop has gained popularity as a remote desktop software. However, users and businesses wonder how secure their systems and data can be with this remote desktop software.
In this article, we’ll talk about the built-in security features of Splashtop and previous vulnerabilities and common attack vectors. We’ll also explore some best practices to improve your remote access security.
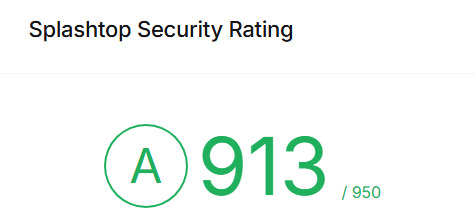
Splashtop Security Rating by UpGuard:
What Makes Splashtop Secure?
Ever wondered whether Splashtop security is safe enough? You might have even asked the question: can Splashtop be trusted? That’s precisely what we will answer in this section.
Splashtop organizes user data security through strong measures and industry compliance, creating a secure remote access solution for businesses, individuals, and educational institutions.
In addition, Splashtop prioritizes securing your data’s privacy and safety for all remote access needs.

Identification and Access Control
Password Protection: Splashtop users can set up strong passwords for their accounts with multi-factor authentication (MFA) support. Also, a secondary authentication method, such as a mobile application or a one-time code sent to your phone, increases your Splashtop account’s security.
Access Permissions: Users can remotely authorize who can use their computers by setting up access permissions. This ensures that only authorized individuals can have access to the remote computer.
Compliance and Certifications
Splashtop obeys several industry standards and regulations, providing users with security and privacy. Some of these industry standards include:
HIPAA Compliance: Is Splashtop HIPAA compliant? Absolutely. Splashtop adheres to all the requirements for handling delicate healthcare data, making it suitable for healthcare professionals.
GDPR Compliance: Splashtop sticks to the General Data Protection Regulation, guaranteeing that user data privacy rights are respected.
SOC 2 Compliance: SOC 2 compliance shows that Splashtop’s service provider follows rigorous security and privacy standards.
Encryption and Data Security
Transport Layer Security (TLS): Splashtop uses TLS encryption to safeguard data during transmission. This widely recognized encryption protocol ensures data protection between local and remote computers.
End-to-End Encryption: Based on Splashtop’s security concerns, it provides end-to-end encryption for specific subscription plans, ensuring data protection from the service provider. This extra layer of security is crucial for delicate data and privacy-conscious users.
A Wide Range of Security Features
Splashtop security features include file transfer control to prevent unauthorized data transfer, a blank screen option for privacy, session recording for auditing and monitoring, and blacklisting/whitelisting to control remote access, providing many security options for users.
Splashtop Security Vulnerabilities
No matter how strongly you build a system, it can’t escape security vulnerabilities at least once in its lifespan. Malicious actors constantly find vulnerabilities in systems and exploit them to break into them.
Specific Resolved Vulnerabilities
- • CVE-2020-12431: The vulnerability, CVE-2020-12431, in Splashtop Software Updater versions before 1.5.6.16 for Windows exposed privilege escalation in 2020.
- • CVE-2023-3181: Another vulnerability was found recently in Splashtop that affected Splashtop Software Updater for Windows versions 1.5.6.21 and earlier. It allowed authenticated local users to manipulate insecure directories and temporary files. That way, those users could escalate privileges to the system level. Because the exploit was easier to execute but had the potential to cause high impacts, its severity score was high.
- • CVE-2024-42050: This vulnerability was related to the Splashtop Streamer for Windows MSI installer. Versions prior to 3.7.0.0 had an issue that could have been exploited.
- • CVE-2024-42052: This vulnerability also affected the MSI installer for Splashtop Streamer on Windows, specifically versions before 3.5.8.0. It was a local privilege escalation issue where a local user could exploit a temporary folder with weak permissions to gain SYSTEM-level access.
- • CVE-2023-5363: In an update to its OpenSSL library, Splashtop version 3.6.4.0 addressed a number of CVEs, including CVE-2023-5363.
Common Attack Vectors and Risks for Remote-Access Tools Like Splashtop
- • Weak passwords: Oftentimes, people don’t use strong and complex passwords or fail to set up multi-factor authentication (MFA) on their accounts. Gaining unauthorized access to systems becomes a piece of cake for attackers. This leaves your personal and business systems and data at risk of being stolen, manipulated, or deleted.
- • Unpatched/outdated software: Unpatched software or software with old versions can have vulnerabilities, such as CVE-2020-12431 and CVE-2023-3181. If cybercriminals can identify them, they won’t take long to exploit these vulnerabilities and compromise your systems and files.
- • Poor configurations: Insecure network configurations, such as weak firewall security and leaving endpoints exposed, could make the network devices and users vulnerable to malicious interception. This could happen despite using encryption protocols, such as TLS or AES-256.
Best Practices to Prevent Splashtop Vulnerabilities
It is essential to stay alert and adapt to best practices for potential threats like hacking. Below are some best practices to follow in protecting your Splashtop account from being attacked by hackers, as well as maintaining a remote access environment:
Strong authentication:
- • Employ strong and unique passwords for your Splashtop accounts.
- • Allow multi-factor authentication (MFA) to add an extra layer of security.
Control access:
- • Use access controls to authorize who can connect to your devices remotely.
- • Frequently review and update access permissions when necessary.
Regular software updates:
- • Always keep your Splashtop application updated.
Secure your devices:
- • Ensure the operating systems and software of your computers are secure as well.
Network security:
- • Always use a secure and well-configured network when using your Splashtop software.
- • Avoid using unsecured or public networks for remote access.
Firewall configuration:
- • Set your firewalls to allow Splashtop traffic while blocking unauthorized access.
Audit and monitoring:
- • Avoid leaving remote connections open when not in use. Ensure to close sessions when they are no longer needed.
User education:
- • Provide users with adequate information about the best security practices and potential risks when using Splashtop.
Endpoint security:
- • Utilize endpoint security measures on your remote device to protect against malware and potential threats like hacking.
Vendor security:
- • Be updated on Splashtop’s security practices, compliance with industry standards, and certifications.
The Best Secure Splashtop Alternative
Looking for a reliable Splashtop alternative that provides better performance and security? HelpWire is a free remote support software that provides you with a seamless and secure remote desktop connection.
HelpWire’s fast connection speed and enhanced performance make it stand out. Some of its free features include file transfer, one-click remote connection, real-time chat, and multiple chat sessions.
HelpWire’s Top Security Features:
Trustworthy Authentication
Confirm your credentials are safe and secured with HelpWire’s integrated authentication and authorization platforms.
Secure Data Transfer
During remote support sessions, all data gets safely transferred via the WSS and HTTPS protocols.
TLS/SSL and AES encryption
HelpWire uses TLS/SSL protocols and AES-256 encryption to ensure safe and secure remote connections to user’s computers.
Secure Data Centers
HelpWire’s data storage is cloud-based and stored on AWS servers.
Permission-Based Access
External operators must seek user authorizations before accessing their remote desktops. This ensures the user’s comfort and confidence.
Signed Applications
HelpWire’s applications are digitally signed by GlobalSign for maximum integrity assurance.
Conclusion
Splashtop offers robust security features for remote desktop access, emphasizing strong user data protection, compliance with industry standards, and a suite of security tools designed to safeguard against various cyber threats. However, it’s crucial for users to also adopt best practices such as employing strong and unique passwords, enabling multi-factor authentication, keeping the software updated, and educating users on security awareness. These practices significantly enhance the security posture when using Splashtop or any remote access tool. Additionally, for those seeking alternatives, HelpWire provides an equally secure and feature-rich option, emphasizing fast connection speeds, secure data transfers, and comprehensive authentication methods.