Is TeamViewer Safe? Everything about TeamViewer Security Issues
The growth of the mobile workforce has made it important for companies to implement remote access solutions for their employees. People need to use applications and access information stored on company computers from their home offices or while on the road. Without reliable connectivity, remote work is impossible.
Any remote connectivity tool must offer robust security to protect communication and sensitive data resources. TeamViewer is a popular software solution that enables individuals to remotely connect to business systems. It’s used by a wide variety of companies to support their mobile workforces.
There have been some TeamViewer security issues that raise questions about the tool. How secure is TeamViewer? Is TeamViewer safe to use for all types of organizations? These are important questions that can influence your choice of secure remote access tool for your business. So let’s consider all these questions in our article.
Useful tip:
Security concerns might be a notable issue with TeamViewer. For assured safety during remote access and to protect personal data, opting for an alternative like HelpWire is advisable. HelpWire utilizes top-tier encryption and robust authentication techniques, ensuring secure connections for both support professionals and their remote clients.
Is TeamViewer Safe and Secure?
TeamViewer employs RSA-4096 key exchange and AES 256-bit encryption to protect data transmission. It also allows users to set up two-factor authentication so remote connectivity cannot be established with just a password. These are powerful security features, but addressing TeamViewer security risks requires the tool to be correctly configured and users to take proactive action.
We’re going to look into past TeamViewer security risks and the steps users can take to make the solution more secure. TeamViewer can be safe if configured correctly and if users take the steps necessary to protect their remote sessions. Yet according to security experts, it may be better suited for individual and private use rather than as the remote access solution for a large enterprise.
Known TeamViewer Security Issues
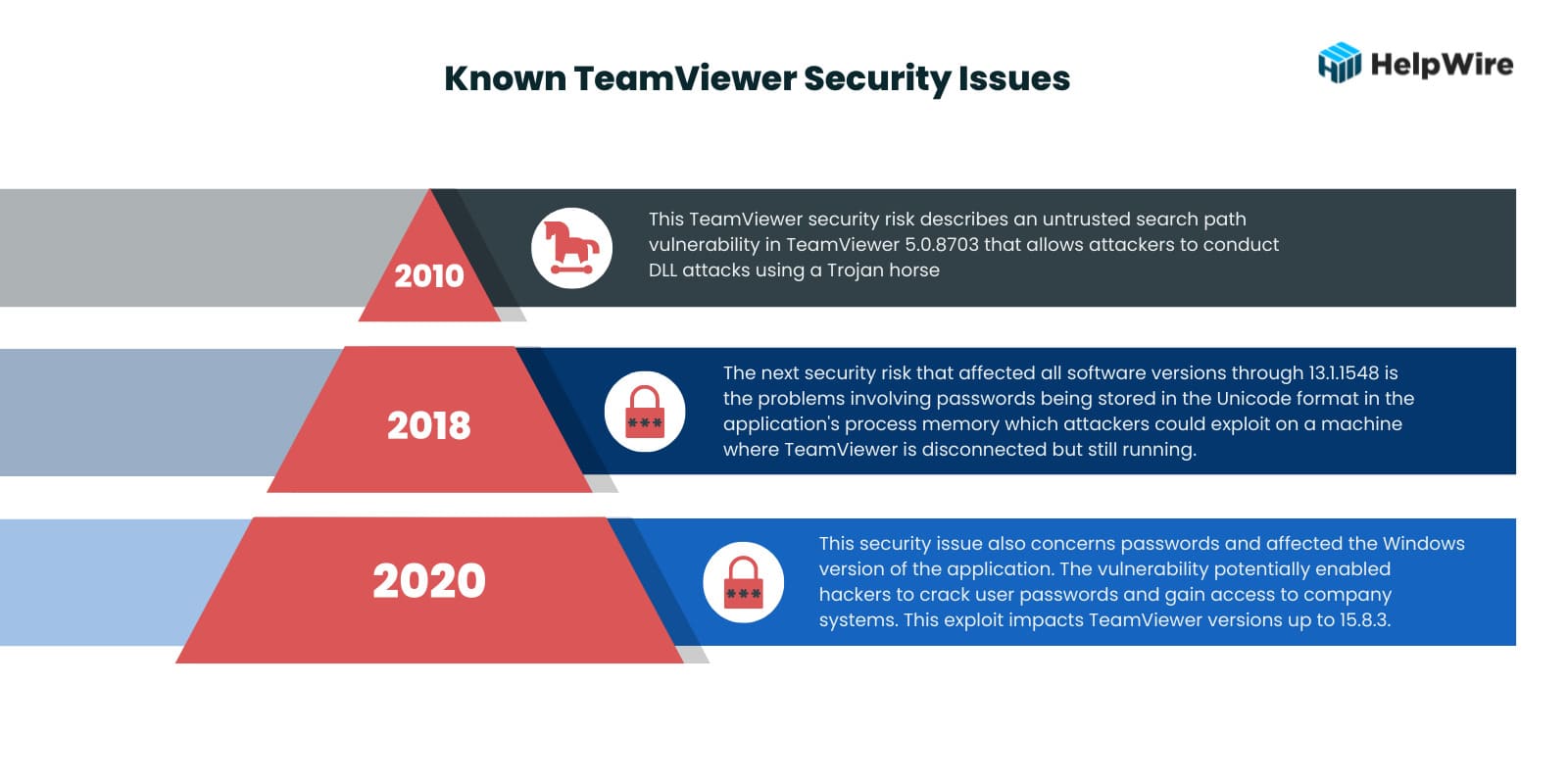
Let’s look at some of the past TeamViewer security issues to get a sense of what types of vulnerabilities the software presents. Several noteworthy security issues have plagued the tool over its lifetime.
- • 2010 – This TeamViewer security risk is documented in CVE-2010-3128. It describes an untrusted search path vulnerability in TeamViewer 5.0.8703 that allows attackers to conduct DLL attacks using a Trojan horse.
- • 2018 – Another TeamViewer security risk that affected all versions of the software through 13.1.1548 is detailed in CVE-2018-14333. The problems involved passwords being stored in the Unicode format in the application’s process memory which could be exploited by attackers on a machine where TeamViewer is disconnected but still running.
- • 2020 – The TeamViewer security issue described in CVE-2020-13699 also concerns passwords and affected the Windows version of the application. The vulnerability potentially enabled hackers to crack user passwords and gain access to company systems. This exploit impacts TeamViewer versions up to 15.8.3.
The vulnerability identified in 2020 was present in all prior releases of the tool beginning with version 8. Once discovered, it was addressed with patches for the affected versions. This fact highlights the importance of updating TeamViewer with the latest patches for the version you are using and migrating to newer versions that may provide enhanced security. The best defense against TeamViewer security risks is to use version 15.8.3 or later releases of the software.
What are the main TeamViewer security risks?
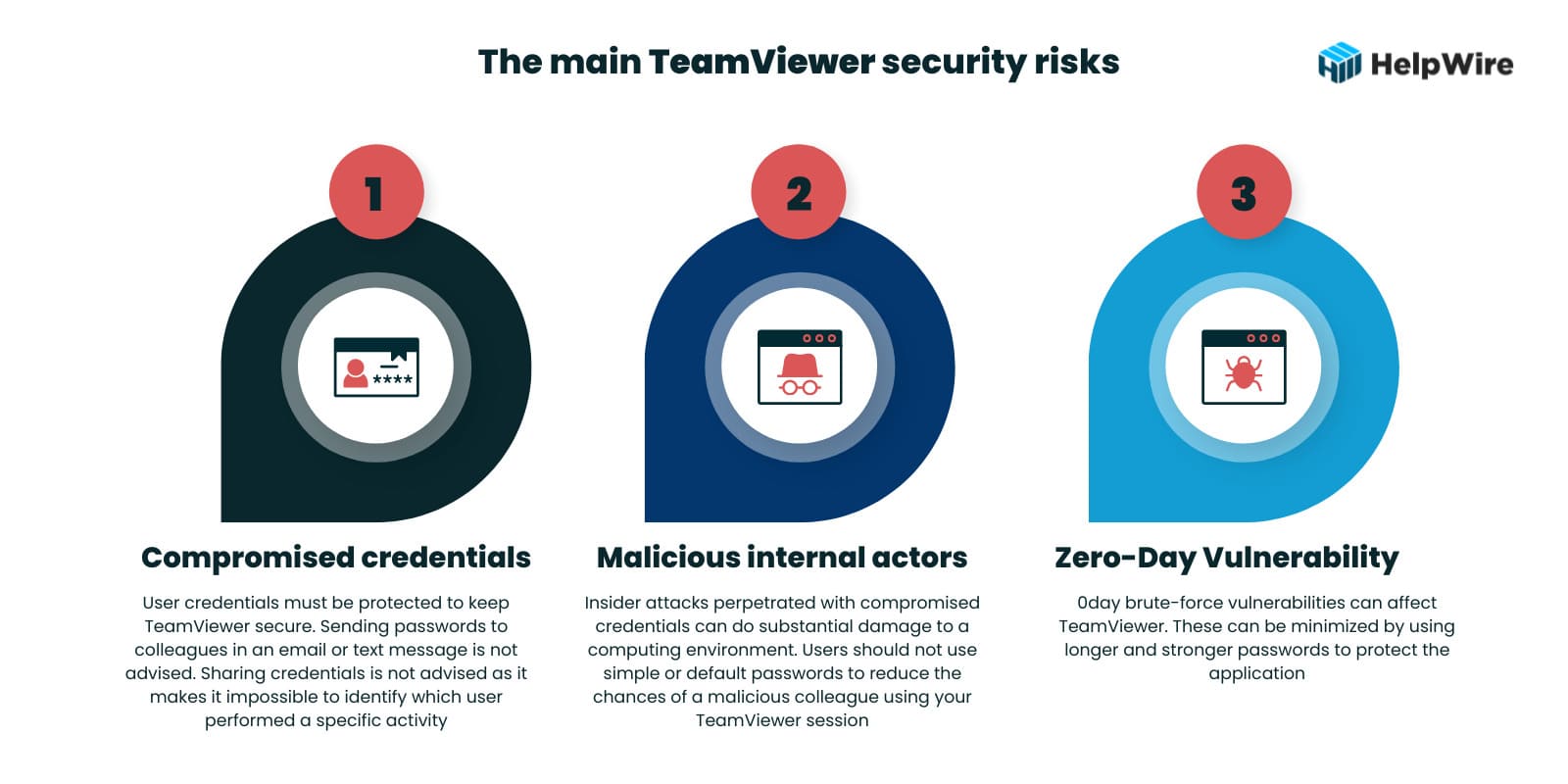
After looking at previous security issues, the question may be “Is TeamViewer safe now?” The majority of TeamViewer security issues fall into three categories.
- • Compromised credentials – User credentials must be protected to keep TeamViewer secure. Sending passwords to colleagues in an email or text message is not advised. Sharing credentials is not advised as it makes it impossible to identify which user performed a specific activity.
- • Malicious internal actors – Insider attacks perpetrated with compromised credentials can do substantial damage to a computing environment. Users should not use simple or default passwords to reduce the chances of a malicious colleague using your TeamViewer session.
- • 0day vulnerabilities – 0day brute-force vulnerabilities can affect TeamViewer. These can be minimized by using longer and stronger passwords to protect the application.
Many TeamViewer security issues are related to weak passwords and the sharing or lax protection of user credentials. These problems can be addressed to a certain extent with user education and the enforcement of strong password policies. Limits on the length of TeamViewer passwords affect their strength and may lead to security vulnerabilities.
10 Steps for Better TeamViewer Security
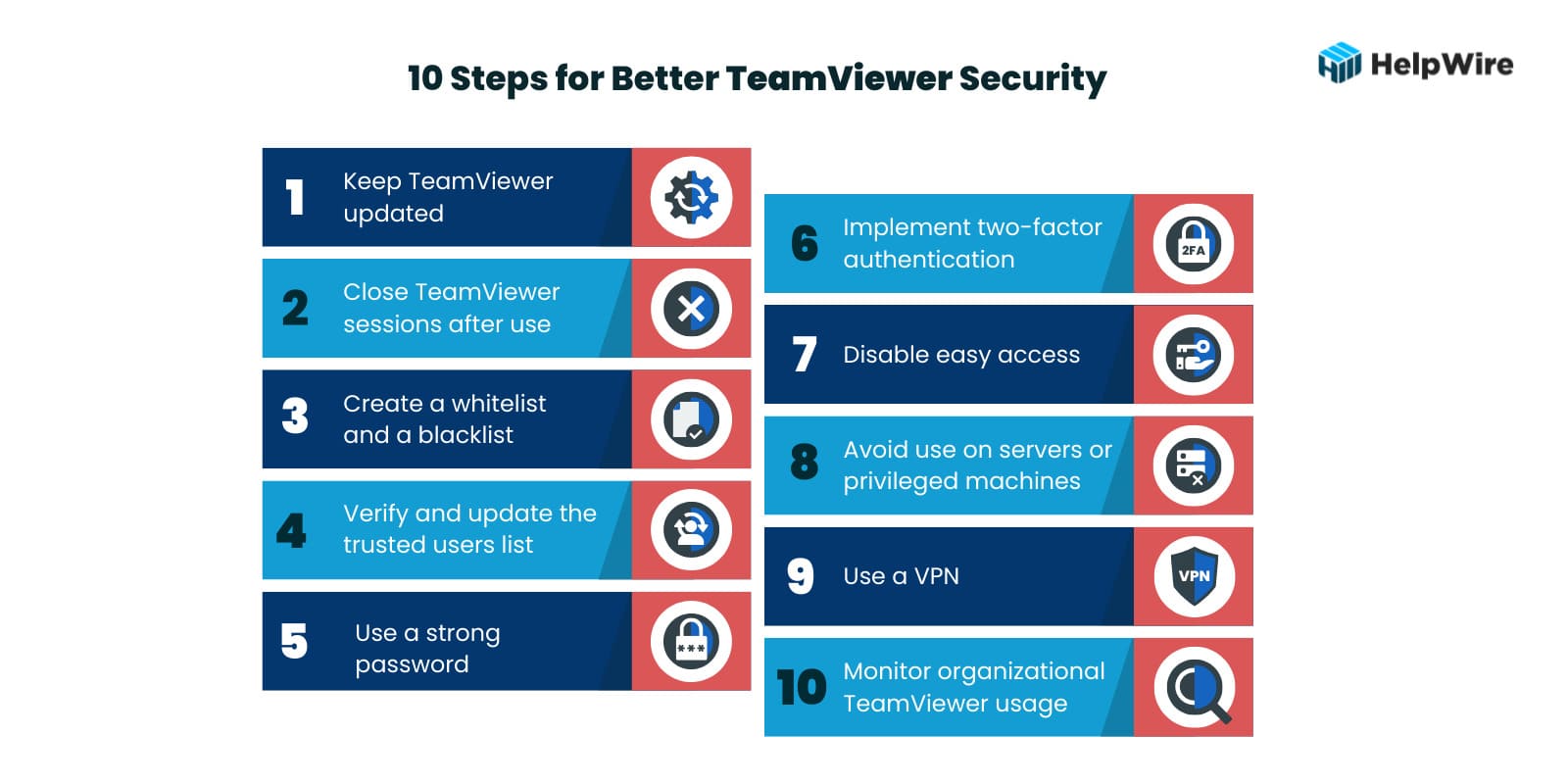 Is it safe to use TeamViewer? The way the tool is configured and used is a big factor in how safe TeamViewer is as a remote access solution. The following ten steps and tips offer a combination of configuration settings and user behaviors or actions that increase the security of TeamViewer.
Is it safe to use TeamViewer? The way the tool is configured and used is a big factor in how safe TeamViewer is as a remote access solution. The following ten steps and tips offer a combination of configuration settings and user behaviors or actions that increase the security of TeamViewer.- Keep TeamViewer updated – Install the most recent updates and any new security patches that address vulnerabilities as soon as they are released. Many users install the program and never upgrade it as long as it still works. This is dangerous as using outdated code can provide hackers with access to your systems.
- Close TeamViewer sessions after use – Don’t run TeamViewer sessions in the background and switch to it when needed. Best practices involve closing a session when not in use and restarting it when necessary. Make sure TeamViewer doesn’t automatically start when you restart your machine. Leaving a TeamViewer session open may enable hackers to gain access to your machine and the wider company network.
- Create a whitelist and a blacklist – TeamViewer allows you to create whitelists and blacklists to control access to a machine. A whitelist lets you limit access to specific users with a TeamViewer account who are added to the list. Creating a blacklist lets you refuse access to entities on the list and avoid potential TeamViewer security risks.
To do this click:
Extras > Options > Security > Configure
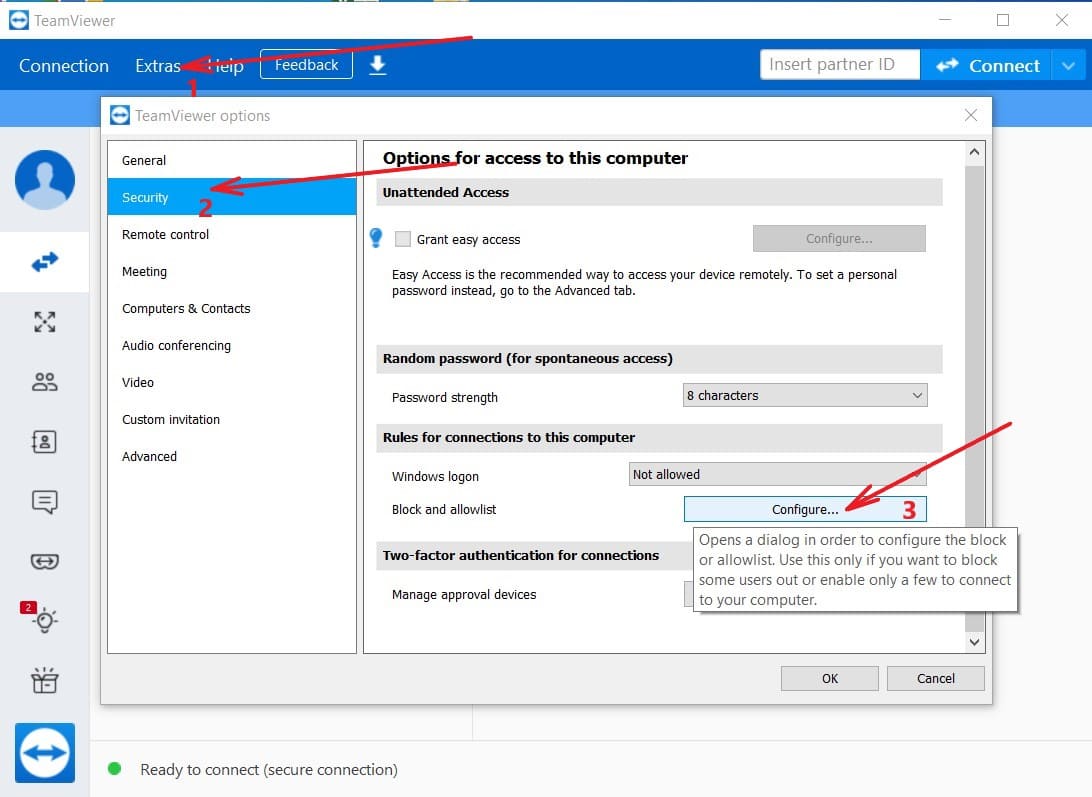
Then choose “Deny access for the following partners” to make Black List or “Allow access only for the following partners” to make White list.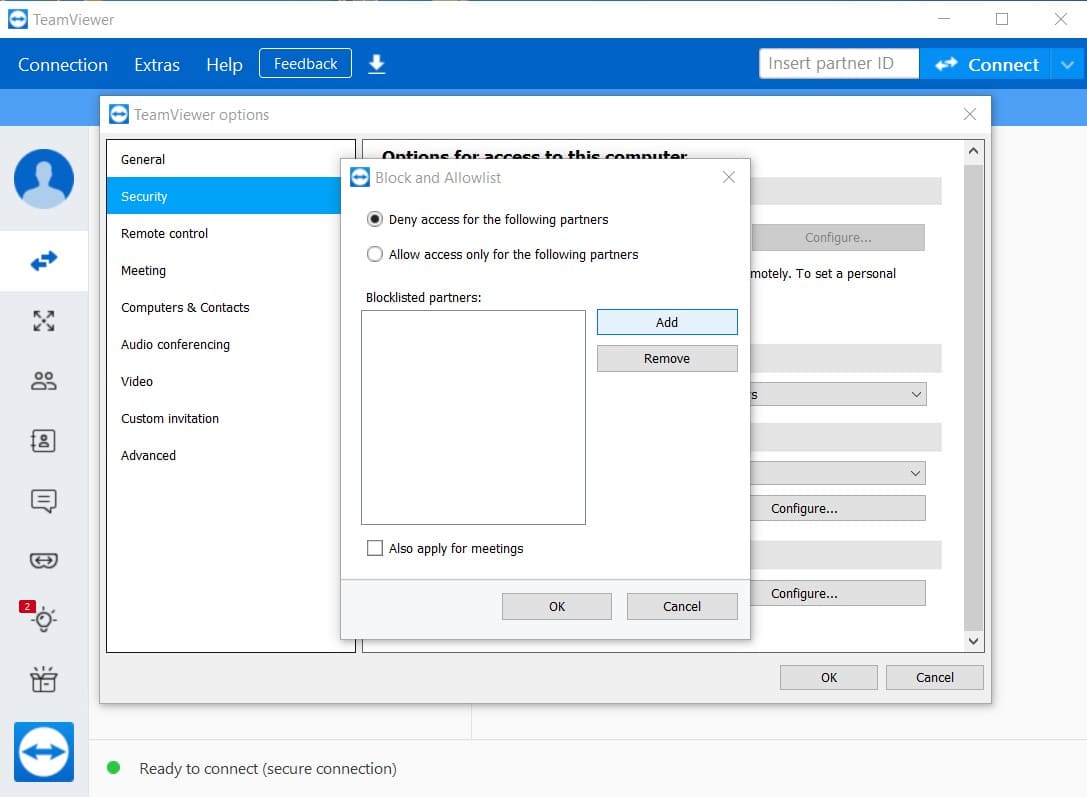
- Verify and update the trusted users list – Verify that you recognize all trusted devices from your TeamViewer profile. Drilling down to Trusted Devices, remove any that you don’t recognize or that should not have access to the given machine
- Use a strong password – When accessing TeamViewer or any application, users need to use a strong password. Trivial or default passwords make it easy for hackers or malicious insiders to compromise your TeamViewer account.
- Implement two-factor authentication – TeamViewer can be configured to use two-factor authentication when establishing a connection. You will need to enter an additional security code when connecting with the application. Two-factor authentication is highly recommended as it eliminates many of the security risks associated with compromised credentials.
- Disable easy access – The easy access option lets devices connect to TeamViewer without a password. Uncheck this option in the Remote Control section to increase security. All TeamViewer connections should require a password.
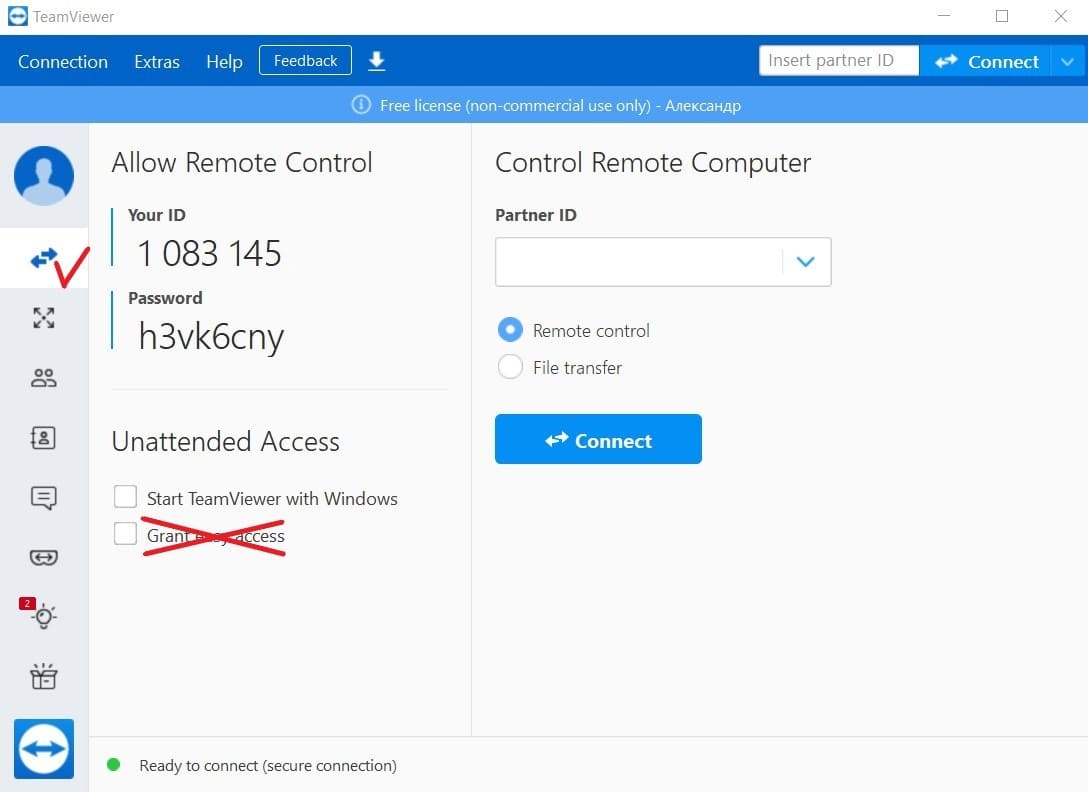
- Avoid use on servers or privileged machines – Potential TeamViewer security risks make it a poor choice for accessing business-critical servers or privileged computers. Use of TeamViewer on these types of machines should be restricted to experienced administrators who understand the tool’s security limitations and how to operate the software safely.
- Use a VPN – A virtual private network (VPN) encrypts data transmission, making it impossible for hackers to steal information or compromise credentials. VPNs protect your data for any type of remote access application.
- Monitor organizational TeamViewer usage – Maintaining security requires an organization to monitor how TeamViewer is used by its employees. This includes understanding what ports the application uses and how it affects other software tools. A company may allow individuals to use TeamViewer to access a subset of computing resources but restrict them from servers or computers that store sensitive data. Usage should be monitored to ensure these policies are followed by all employees.
If you have connecting problems with TeamViewer after these settings, find out what are the most common TeamViewer issues and how to solve them.
Choose trusted, secure remote support software
Why waste time in solving TeamViewer security issues when you can use a secure substitute?
HelpWire is an intuitive remote desktop service designed for small to medium-sized businesses. It provides a fast, direct, and secure remote access solution. Moreover, it enables a cost-free, smooth connection to PCs or Macs.
Not only that, but HelpWire takes its users’ safety seriously:
• Robust Authentication Security
Maintain the safety of your credentials with our robust authentication and authorization system, Auth0.
• Advanced Encryption Protocols
Employing TLS/SSL protocols along with AES-256 encryption, HelpWire guarantees robust security for remote connections to client devices.
• Secure Data Centers
HelpWire’s server framework is securely hosted on cloud platforms, utilizing AWS servers for enhanced protection.
• Certified Application Security
Each HelpWire native application is digitally certified by GlobalSign, ensuring enhanced security and integrity.
• Consent-Based Remote Access
Clients have full control over access to their workstations, with HelpWire requiring explicit client approval for operator access, thereby bolstering trust and privacy.
• Immediate Access Revocation
Clients can instantly terminate an operator’s remote access to their workstation, either through a global keyboard shortcut or a dedicated button within the HelpWire Client application.
Final Thoughts
We earnestly hope this article has alleviated any concerns you might have had regarding TeamViewer. With a comprehensive range of solutions now at your disposal, you should feel more capable and ready to effectively address these challenges.
FAQ
Why are TeamViewer Firewall settings important?
Companies can enhance security through the use of a corporate firewall that blocks unknown outbound connections. Collecting logs from the firewall will identify TeamViewer sessions that a company may want to restrict. Users can be notified that TeamViewer is not allowed in those situations.
The logs will also show all traffic attempting to access TeamViewer. This information can be used to create firewall rules to block IP addresses and restrict access to the network. All TeamViewer outbound connections go through the firewall. A strict firewall policy can be created that blocks all inbound traffic and only opens port 5938 for outgoing connections.
Is TeamViewer safe for personal use?
How do I check TeamViewer's log files?
Following are some examples of viewing TeamViewer log files.
Windows or macOS systems:
- Open the TeamViewer window and click Extras -> Open Log Files.
- Locate the file called “TeamViewerXX_Logfile.log“, where XX is your TeamViewer version.
- Include the “TeamViewerXX_Logfile_OLD.log” file if it exists.
iOS devices
TeamViewer Remote Control/TeamViewer Meetings
- Click Settings in the far right of the app menu at the bottom of the screen.
- Select Show log file from the menu.
TeamViewer QuickSupport
- Click the three dots ( … ) in the upper right corner of the app.
- Select Advanced.
- Select Log Files.
Android devices
TeamViewer Remote Control
- Click the three dots ( … ) in the upper right corner of the app.
- Select Settings.
- Select Log files.
TeamViewer Host
- Click the three dots ( … ) in the upper right corner of the Host login screen.
- Select Advanced.
- Select Log files.
More complete information about accessing log files in various ways is available on this page.
What ports does TeamViewer use?
TCP/UDP Port 5938
Its preferred method of establishing outbound connections is through TCP/UDP Port 5938. In a TeamViewer environment, your firewall should have this port open. TeamViewer demonstrates the best performance when using port 5938.
TCP Port 443
If the preferred port 5938 is not available, the next choice for TeamViewer connections is port 443. The iOS and Windows Mobile apps do not use this port. When deploying custom modules with a Group Policy defined in the Management Console, ensure port 443 is open on all machines that will use the application. TeamViewer also uses port 443 to check for updates.
TCP Port 80
When ports 5938 and 443 are not available, TeamViewer will try to connect over TCP port 80. Port 80 is only used as a last resort for several reasons. It’s less reliable than the other ports and offers slower connection speed because of additional overhead requirements. There is also no automatic restart for lost connections. Android and iOS devices may use port 80, but Windows Mobile does not allow it.
Windows Mobile
The Windows Mobile platform restricts apps to using a single outbound port. Connecting out from the device requires the use of port 5938. You may get a message telling you to check your Internet connection when using TeamViewer on a mobile device. This is most likely caused by that port being blocked by your router, firewall, or the data provider.