How To Enable Remote Desktop Remotely: A Definitive Guide
Many support professionals know what it’s like when they’ve just completed work on a client’s workstation but still, they’ll need remote access to the machine to finalize or fix loose ends in the future using Remote Desktop.
Windows and Windows Server versions do not have Remote Desktop enabled by default, but it can be easily done via the Control Panel if the computer is right near you.
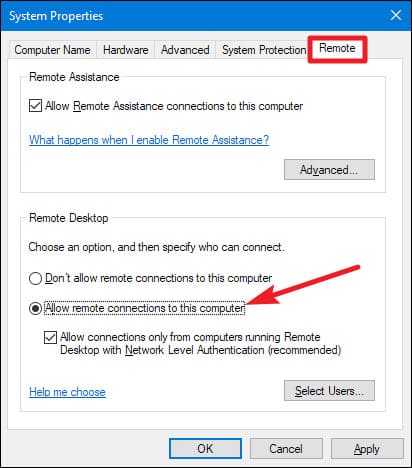
However, if Remote Desktop is disabled due to security measures, enabling it remotely when the machine isn’t physically present in front of you can be tricky.
Below, we’ll explain how to remotely enable Remote Desktop Windows 10 using Group Policy, PowerShell, WMI, or psexec without local access to the target computer. By the end of this article, readers will know how to turn on Remote Desktop remotely and connect to a client computer when it needs to be fixed.
How to turn on RDP remotely using Group Policy
Follow the steps below to enable Remote Desktop remotely with Group Policy:
- Launch your Group Policy Management Console (GPMC).
- Generate a new Group Policy Object, or edit an existing GPO.
-
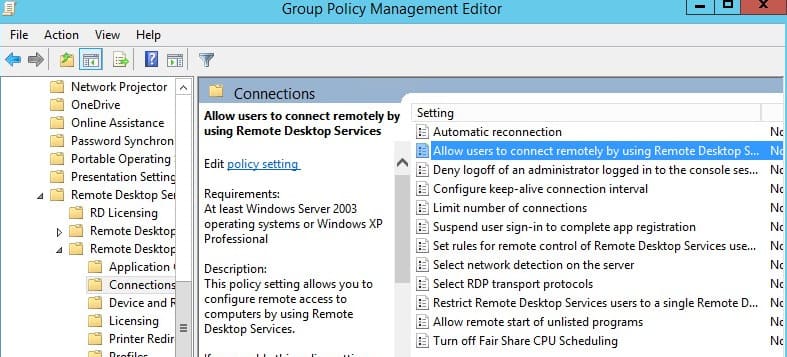
Navigate to the GPO node below:
Computer Configuration\Administrative Templates\Windows Components\Remote Desktop Services\Remote Desktop Session Host\Connections -
Double-click “Allow users to connect remotely by using Remote Desktop Services” (shown below).
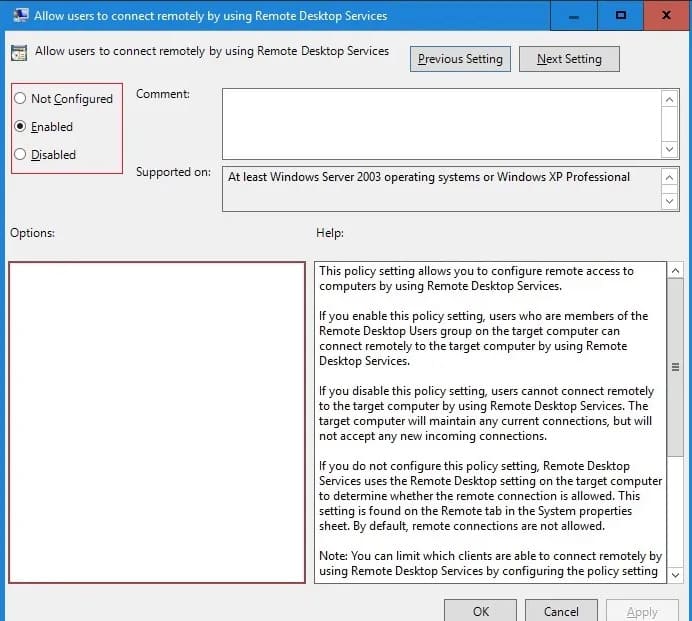
-
Choose “Enabled” radio-button and hit OK.
- Close the GPO editor.
-
Link the Group Policy Object (GPO) to the appropriate Organizational Unit.
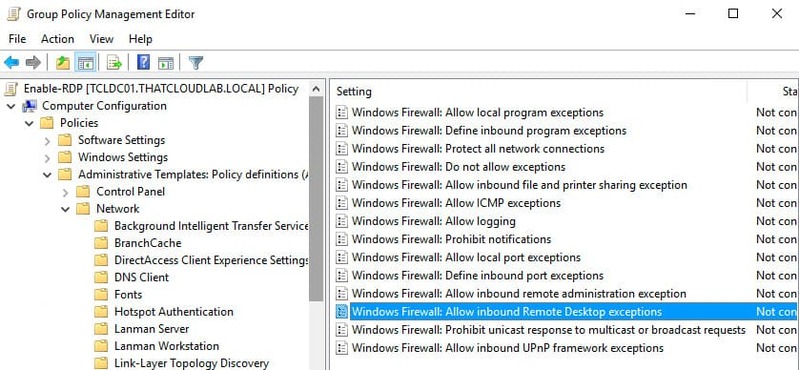
To remotely enable RDP, users must permit RDP in the Windows Firewall located on the remote Windows 10 computer. Navigate as follows:
Computer Configuration > Policies > Administrative Templates > Network > Network Connections > Windows Firewall > Domain ProfileAnd set “Allow Inbound Remote Desktop exceptions” to Enabled.
The one main issue with Group Policy is that for users who need quick log-ins to remote machines, Group Policy isn’t a viable option.
Adversely, a PowerShell console allows users to accomplish the task with a single command.
How to enable Remote Desktop remotely with PowerShell
Turning on Remote Desktop remotely entails configuring and running WinRM service (Windows Remote Management) on the remote machine. Beginning with Windows Server 2012, WinRM services are enabled by default in all subsequent versions.
However, WinRM isn’t activated on client operating systems (like Windows 10) by default.
Remote computers must meet the standards outlined below to enable Remote Desktop via PowerShell:
- — Run the WinRM service.
- — Users must have administrative permission on the remote computer.
- — Windows Defender Firewall with Advanced Security should be disabled or users should enable the rules permitting remote access via PowerShell Remoting.
Here is an example for users who want to turn on RDP remotely via Windows Server 2012 R2/2016/ 2019.
- Run the PowerShell console on your computer.
- Run the command (shown below) to connect with a server remotely:
Enter-PSSession -ComputerName server.domain.local -Credential domainadministrator
Note: Once users establish a remote session, they can begin executing PowerShell commands on it.
To enable Remote Desktop, users must edit registry parameter fDenyTSConnections on the remote machine from 1 to 0.
Run the following command:
Set-ItemProperty -Path 'HKLM:\System\CurrentControlSet\Control\Terminal Server'-name "fDenyTSConnections" -Value 0
When enabling RDP using this method, the rule allowing remote RDP connections is not enabled within the Windows Firewall rules.
Run the command below to allow incoming RDP connections in Windows Firewall:
Enable-NetFirewallRule -DisplayGroup "Remote Desktop"
Here’s a tip: On Windows computers, TCP/3389 ports are used for incoming Remote Desktop connections by default. Users can alter the default RDP port number in the registry via the PortNumber parameter in the reg key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp.
If the above firewall rule is missing, create it manually using the command below:
netsh advfirewall firewall add rule name="allow RemoteDesktop" dir=in protocol=TCP localport=3389 action=allow
Restrict hosts and/or subnets allowing users to connect with Remote Desktop by creating a custom rule permitting Windows Firewall to only accept incoming RDP connections from specific IP addresses, subnets, or IP ranges.
In this scenario, use the following command instead of the previous one:
New-NetFirewallRule -DisplayName “Restrict_RDP_access" -Direction Inbound -Protocol TCP -LocalPort 3389 -RemoteAddress 192.168.1.0/24,192.168.2.100 -Action Allow
Enable secure RDP authentication (NLA – Network Level Authentication) by running the following command:
Set-ItemProperty -Path 'HKLM:\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp' -name "UserAuthentication" -Value 1
Check the availability of TCP port 3389 on the remote host from your computer by running the command:
Test-NetConnection 192.168.1.11 -CommonTCPPort rdp
Note: This means RDP on remote hosts are enabled, allowing users to establish remote desktop connections using mstsc.exe or other 3d-party RDP client.
If a situation arises where users must enable RDP on multiple remote computers at once, use the following PowerShell script:
$comps = “Server1”, “Server2”, “Server3”, “Server4”
Invoke-Command –Computername $comps –ScriptBlock {Set-ItemProperty -Path “HKLM:\System\CurrentControlSet\Control\Terminal Server” -Name “fDenyTSConnections” –Value 0}
Invoke-Command –Computername $comps –ScriptBlock {Enable-NetFirewallRule -DisplayGroup “Remote Desktop”}
Only members of the local Administrators group can connect remotely via RDP by default.
Administrators can enable RDP connections for non-admin users by adding them to the local Remote Desktop Users group.
Add desired users to the Remote Desktop Users locally via the Local Users and Groups (LUSRMGR.MSC).
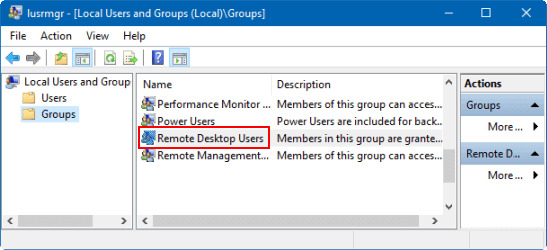
Another option is altering RD Users group membership remotely with PowerShell Remoting’s Enter-PSSession.
Enter the following command to add the domain user “jdoe” to the local group:
net localgroup "remote desktop users" /add "test\jdoe”
Alternatively, users can try another PowerShell remoting command (“Invoke-Command”) instead of the Enter-PSSession:
Invoke-Command -Scriptblock {net localgroup "remote desktop users" /add "test\jdoe”
} -Computer server.test.com
Enabling remote desktop remotely with WMI
To enable RDP on remote computers where WinRM is disabled (like on a regular computer with Windows 10), users can try the WMI PowerShell command.
Check whether RDP access is enabled on the remote computer by running the command:
Get-WmiObject -Class Win32_TerminalServiceSetting -Namespace root\CIMV2\TerminalServices -Computer 192.168.1.11 -Authentication 6
Add a Windows Firewall exception rule to enable RDP with the command below:
(Get-WmiObject -Class Win32_TerminalServiceSetting -Namespace root\CIMV2\TerminalService
How to enable RDP with psexec
The last method discussed in this article involves the free Microsoft tool, psexec. This remote access option won’t need PowerShell remoting enabled, but it is not as straightforward.
Psexec needs Windows Firewall open for File and Printer sharing, which is likely more common than opening WMI ports or enabling PowerShell remoting.
Navigate as shown below:
Computer Configuration > Policies > Administrative Templates > Network > Network Connections > Windows Firewall > Domain Profile > Windows Firewall: Allow inbound file and printer sharing exception
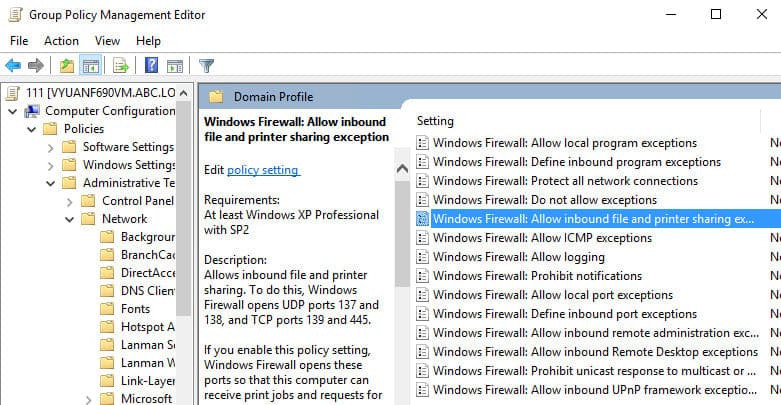
Edit the registry to enable RDP with psexec by executing the below command:
psexec.exe \\<computer name> reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
This command also sets the registry key, which disables Terminal Server access to 0.
Permit Remote Desktop Protocol (RDP) connections in Windows Firewall with psexec:
psexec.exe \\<computer name> netsh firewall set service RemoteDesktop enable
Summing up
As you can see, users have multiple options to experiment with enabling Remote Desktop remotely. While the methods discussed have their pros and cons, all are accessible enough for users of all ilk to experiment with and find their ideal option.
In the modern era, remote access is not only convenient — but necessary. As the working world continues to shift toward remote working environments, organizations of all sizes should implement safe and secure remote access procedures to ensure uninterrupted productivity for their team.