IoT Standards and Protocols Guide
Why IoT System Needs Protocols in a First Place
Despite their popularity, IoT devices are built on different layers that allow them to perform between task input and result presentation. This invisible infrastructure, often called IoT communication protocols, allows all hardware and softwares to communicate before executing an assigned task.
If you work in the smart tech industry, you may have wondered, “What are IoT protocols?”. In simple terms, the Internet of Things protocols refer to a set of rules that govern the transmission of data between electrical devices. These rules are preset agreements that detail the structure of information flow and how each device relates to the other.
IT teams have to spend time understanding the communication protocols in IoT and concern themselves with the integrity of data transfer systems. To understand the protocols behind the internet of things and why they matter, it helps to have an overview of how an IoT operates.
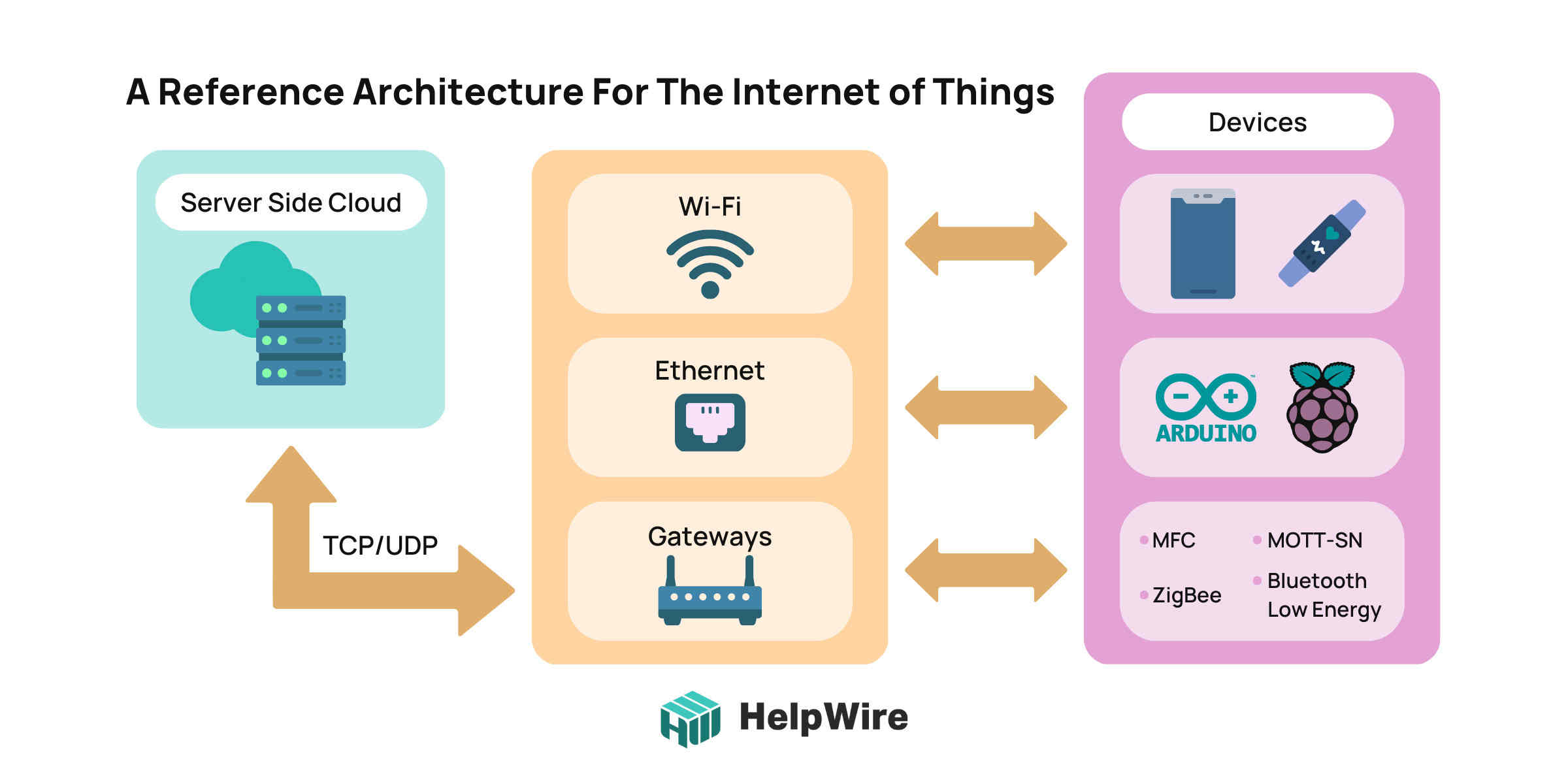
A typical IoT structure involves four building blocks:
- • A collection of smart technology that receives data and performs specific tasks.
- • Gateways and networks that allow IoT technology enter and connect with the internet.
- • Tech applications that help users manipulate their space.
- • A software platform heavily responsible for providing storage space as well as advanced computing technology.
In General, Two Classifications of IoT Protocols Exist:
IoT Network Protocols
These sets of IoT networking protocols connect devices over the internet. They allow end-to-end communication systems within the network’s scope.
IoT Data Protocols
These IoT standard protocols are distributed through a wired or cellular network. They connect low-technology devices with other hardware without needing an internet connection.
The Connectivity Layer: A Simple Magic Zone
The connectivity layer of an IoT architecture is responsible for data transmission across devices, cloud services, and networks involved in the structure. There are major ways teams ensure smooth connectivity between devices.
This list of IoT protocols includes the following.
Via TCP/UDP/IP Stacks
These stacks allow communication between devices over long distances. The Transmission Control Protocol (TCP) is specifically engineered to offer a reliable, end-to-end stream over networks that aren’t stable. A TCP establishes a duplex virtual circuit between transmitting hosts, allowing both hosts to simultaneously put data over the internet without specifying a destination.
Via IoT Gateways
IoT gateways are centralized hubs consisting of software and hardware modules that connect cloud-based systems and data-processing analytics softwares to sensors and other intelligent devices.
These modules act as translators between different protocols, handling inbound and outbound traffic from different devices. Gateways are also responsible for encrypting and decrypting data in IoT devices. As a result, they play special roles in the security of an IoT infrastructure.
Sometimes, these protocols are also responsible for locally preprocessing data before uploading it to a cloud service. Hence, the device may be required to duplicate, aggregate, or summarize data in very small volumes to help improve response times and reduce network transmission costs.
Data Transfer Technologies in IoT System
IoT transfer technology varies on a use-by-use case scenario. Here is a breakdown of different data transfer technologies in an IoT system:
Bluetooth
This popular wearable piece of tech is used for short-range communication. These devices are instrumental in situations that require data to be sent in small bits between low-power devices. You can easily spot Bluetooth tech in geolocation sensors and smartphone technology.
Radio-Frequency Identification
RFIDs are devices that primarily use radio waves to determine and track the position of objects within a building. Employed in various commercial and industrial cases, it allows corporations to track items within a supply chain to prevent problems arising from out-of-stock scenarios.
In this wireless tracking tech, the device transmits data between the reader and tag by emitting radio waves.
Wi-Fi
This protocol allows different devices to connect within a specific range. They use radio waves to broadcast information on specific frequencies (2.4 GHz or 5GHz channels).
Wi-Fi devices can be found anywhere as the technology makes it possible to transmit large data over reasonable distances. Regardless of their ubiquity, these devices tend to consume a lot of power.
ZigBee
This wireless network is mainly employed in traffic management, the machine industry, and home automation systems. This low-power technology supports a host of devices, including point-to-point and mesh networks. Construction businesses looking for low-cost and reliable wireless technology often rely on ZigBee tech. An amazing feature about this technology is that it can carry small pockets of data over a wide distance range.
IoT Security Protocols
IoT networks and protocols allow smart devices to communicate with one another and other IoT cloud platforms, and this communication often involves the transmission of sensitive data. Due to their scalability and affordability, many IoT protocols are open-source codes that businesses can easily purchase and customize on a case-by-case basis.
As open-source technology continues to rise, many data packets are vulnerable to hacking and corruption, which can lead to disastrous consequences in real life. It, therefore, becomes increasingly important to worry about the security of your company’s connectivity channels.
IoT security refers to the different tools, strategies, and processes teams use to secure all aspects of IoT, including the protocols in use. A robust approach to IoT security requires that cyber security teams focus on protecting the integrity of network connections and the IoT ecosystem.
Here are the top 5 Security Protocols for the Internet of Things:
MQTT
Messenger Queue Telemetry Transport (MQTT) is the first security system on our list. One of the most widely used security mechanisms in the IoT is MQTT. Dr. Andy Stanford-Clark and Arlen Nipper created the client-server messaging transit system in 1999. MQTT uses TCP/IP or other protocols that offer specified, lossless, two-way connections to operate.
One advantage of MQTT is that it has a straightforward, incredibly lightweight system that makes data transfer simple and quick. In addition, MQTT is intended for low-bandwidth, unstable, or high-latency networks in addition to limited devices. Only a few security methods are specified by MQTT, and it frequently makes use of other security protocols like username/password, VPN at the network level, and SSL/TLS for transit encryption.
CoAP
Constrained Application Protocol (CoAP) is a web transfer algorithm created for low-power or lossy networks, which are limited networks and restricted devices. CoAP is built on the REST paradigm, just like MQTT. Clients use techniques like GET, PUT, POST, and DELETE to access resources made accessible by servers under URLs.
CoAP is made to run on microcontrollers, which makes it ideal for the Internet of Things because it needs millions of low-cost terminals. CoAP also consumes a negligible amount of network and gadget resources. It can function with UDP on IP, which adds to its protection.
DTLS
DTLS is an IoT security mechanism created to safeguard data transmission between apps that use datagrams. It offers the same degree of security and is built on TLS. A retransmission delay is used by DTLS to address the data loss problem. The client retransmits the data if the timer expires before it gets the server’s confirmation notification. By assigning a unique sequence number to each communication, DTLS addresses the problem of rearranging. It is used in situations where latency is more crucial than data loss, such as live video streams, video streaming, gameplay, VoIP, and instant messaging.
6LoWPAN
6LoWPAN is a standard for low-power networks, such as Internet of Things (IoT) devices and wireless sensor networks. It is employed to transport IPv6-formatted data packages over a variety of networks. End-to-end IPv6 is provided by 6LoWPAN, making it possible to link directly to a range of networks, including the internet. 6LoWPAN is additionally used to secure end-user interactions with the sensing network. AES-128 link layer security, as specified by IEEE 802.15.4, is used by 6LoWPAN protection for IoT.
ZigBee
ZigBee is a wireless mesh network protocol for IoT devices that is low-cost and low-power. With minimal power usage, ZigBee devices can create a mesh network that can span a sizable area. The ZigBee system encrypts data transmission between devices using AES-128. Additionally, it offers replay security, message fidelity, and safe bootstrapping. Applications like house automation, intelligent lighting, and energy management frequently use ZigBee.
LoRaWAN
Long Range Wide Area Network (LoRaWAN) refers to a long-range, low-power protocol that primarily deals with signal detection below noise levels. This protocol connects devices over the internet using either private or public networks.
Devices encoded with LoRaWAN connect remotely and provide real-time feedback on specific signals. Due to their low data limits, they do not require a lot of data and power usage.
IoT Security Threats
To understand what security measures your business requires, it helps to know what threats exist.
Sinkhole Attack
The system drops all data packets instead of sending them to the receiver’s destination. All signals from the wireless network are redirected to new nodes that harm the IoT environment.
Denial of Service
DoS attacks happen due to the heterogeneity and complexity of connected IoT devices. These attacks prevent the authentic user from accessing the device or network resources, allowing the hacker to flood the network with redundant requests making it impossible for real users to access.
Man in the Middle Attack
This type of security breach happens when a hacker intercepts and alters the communication between communicating devices. Now that the attacker has complete control over the channel, they can capture and manipulate data in real-time.
Gateway Attack
Unauthorized personnel cut off communication between the internet and internet-connected infrastructure. This attack also encapsulates DoS attacks and routing attacks where false or no information is transmitted from the internet to the receiving nodes.
To protect the transmission of data, here are some measures you can take to protect your business.
- • Encryption keys: These keys provide additional security to messages and data collated from IoT devices. This system converts data into cipher text that non-authentic users can not understand.
- • Authorization and identity management: This mechanism helps to determine user and recipient rights when transmitting data between devices. This determines who has access to each device, authenticates the requests, and prevents any unauthorized entity from changing the data transferred.
- • Secure software execution environment: This software is a protected code and run-time environment designed to prevent unexpected applications or softwares from accessing the system.
- • Software updates: Teams must check consistently for patches and protocol security updates. You may also consider enabling WPA2 security protocols, using strong device passwords, and increasing network security with encryption keys.
- • Route and gateway security: To ensure a secure route, cyber security teams can route data through several paths that expose errors present in the protocols for IoT. Organizations are also encouraged to adopt IoT ecosystems designed with additional security features like crypto engines, tamper detection, and encryption keys.
Other IoT Protocols
Here are examples of the most common IoT protocols on the market:
Advanced Messaging Queuing Protocol (AMQP)
AMQP is an open message standard that uses data queues to allow synchronous communication between connected devices. This standard assists peer-to-peer data exchange between multiple servers.
It also allows devices to manage issues like poor networks and traffic spikes. While it might be a lengthy standard, these protocols used in IoT devices offer additional features like persistent and durable queues, high-availability queues, federation queues, and flexible routing.
Data Distribution Service (DSS)
DDS is an architecture that connects IoT devices to systems that require real-time feedback. It plays an important role in industries like robotics, power generation, and autonomous vehicles, where real-time data is required. DDS focuses on the node of structures built on a subscription or publication-based service model.
Hypertext Transfer Protocol (HTTP)
HTTP is particularly useful for data transmission over the internet and web services. While this protocol is very popular, it isn’t a great choice for IoT devices since synchronous data transmission may face some challenges due to network conditions and often require more power to encode and decode small bits of data.
Narrowband IoT (NB-IoT)
NB-IoT is a radio standard that transmits a lot of data over a wide range of distances with little power. It also uses existing network structures to ensure global coverage and signal quality. NB-IoT devices require low bandwidth, experience long battery life, and allow for a wide range of applications. They fall under the category of LPWAN protocols.
They play key roles in industries where non-cellular standards are found, such as smart agriculture, manufacturing, predictive maintenance, and smart home applications. They are also more popular with stationary devices and assets as opposed to technology that requires mobility and voice features.
LTE-Cat M1
These LPWA standards connect devices that have medium data requirements. It is particularly useful for devices with longer battery lifecycles and allows enhanced in-building range. It rarely requires new infrastructure to be implemented and is particularly useful in mobile use cases.
The Role of IoT Protocols in Protecting Your Business
Like every other revolutionary technology, IoT devices play key roles in modern-day life. Although the IoT architecture changes across projects, a need remains to securely handle large amounts of data that are instrumental to the project’s success. IoT standard vulnerabilities allow cybercriminals to steal sensitive information as it travels through the protocol.
Regardless of the device and channels, choosing the right IoT device protocol for your business depends on a case-by-case basis. When employing IoT in business, stakeholders need to understand how standard IoT protocols work and identify key areas that require optimization and security.
Protecting the protocol connectivity layers means that your business can thrive on privacy without worrying about external interference and any problems associated with insecure network connections.