IoT Architecture Guide. Major and Additional Layers of IoT System
Internet of Things (IoT) is the term used to describe the billions of connected devices that communicate and share data over the Internet. The IoT is not only comprised of Internet-connected sensors and devices but includes the tremendous volumes of data they generate.
IoT’s layered architecture is responsible for collecting, managing, storing, and processing data resources. Four main layers are incorporated into IoT architecture with each playing a critical role in the success of an IoT implementation. Several additional, smaller layers provide enhanced precision to Internet of Things architecture. This article looks at how these layers support the functionality of IoT applications.
What is IoT Architecture?
IoT architecture is a general configuration of fully functional IoT system, where each component is responsible for own set of tasks. The architecture of IoT systems provides IoT implementations with the flexibility that is one of their defining characteristics. IoT systems are used in a wide range of applications spanning virtually every market sector. Despite the variety of ways they are used, systems are built using the same foundational IoT infrastructure layers.
The basic Internet of Things infrastructure is comprised of the following four layers.
Perception – The perception layer is where data is collected from sensors on connected devices and acted upon by actuators.
Connectivity – The connectivity layer is responsible for transferring data and facilitating communication between the devices and networks that make up an IoT system.
Processing – The processing layer is where data resources generated from prior levels are stored and processed to prepare them for use in the subsequent application layer.
Application – The application layer is where pre-processed data is analyzed and used to address a wide range of business requirements such as control systems or advanced analytics.
This process of collecting and processing data from connected devices to solve a business or organizational problem is at the heart of all IoT implementations.
Main Components of IoT Architecture
Let’s take a more detailed look at the major and additional IoT architecture components. Each plays an important role in delivering the expected results of an IoT implementation.
Major IoT Architecture Layers
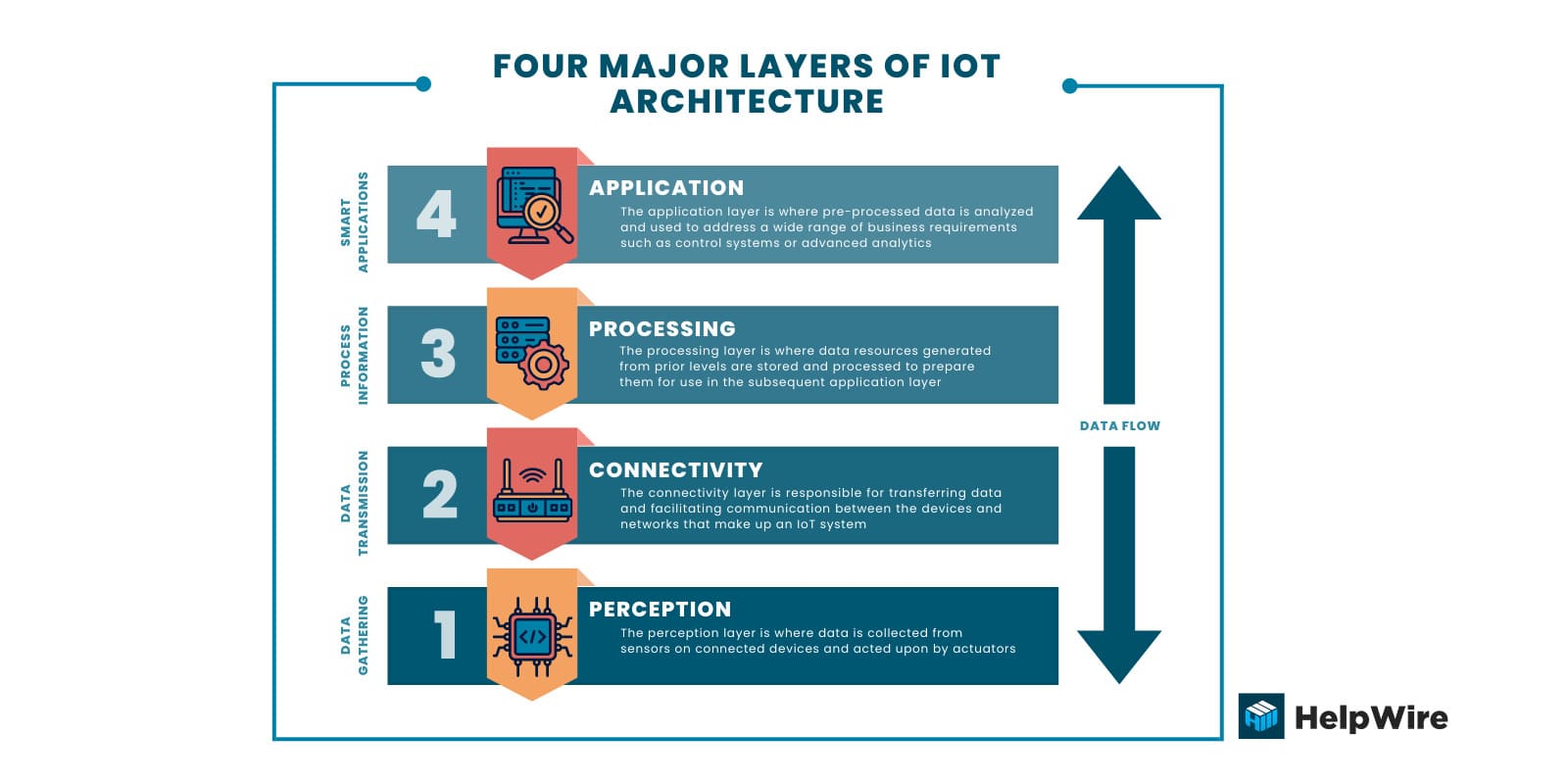
These core components of IoT architecture are present in all IoT implementations. As you will see, there is a wide diversity in how each layer is implemented and differences in the functionality provided based on the way an IoT solution is constructed.
Perception
The primary purpose of the perception layer is to convert between digital and analog signals. This layer forms the foundation of IoT infrastructure as it collects data and may also perform actions based on the collected information. Internet-connected devices or endpoints represent the connection between the digital and physical worlds.
Many different types of devices, running different IoT operating systems, are deployed in the perception layer. These devices are usually broken into three groups.
Sensors – Sensors can take many forms including meters, gauges, and probes. The sensor takes readings of environmental variables such as temperature, pressure, or wind speed and converts the information to digital signals. These signals are then transmitted to cloud platforms for processing.
Actuators – These devices reverse the role of sensors. They convert digital signals sent from the IoT system into physical actions that can be used to control machinery in automated assembly lines or power generating equipment.
Machines and devices – Sensors and actuators are often connected to machines and devices. In some cases, the sensor or actuator is the device’s main component.
Internet of Things architecture has no limitations on the type of devices used in the perception layer nor where they are located. A device can be a miniature sensor or a large piece of industrial machinery. Devices can be confined to a room or encompass millions of points spread around the globe.
Connectivity
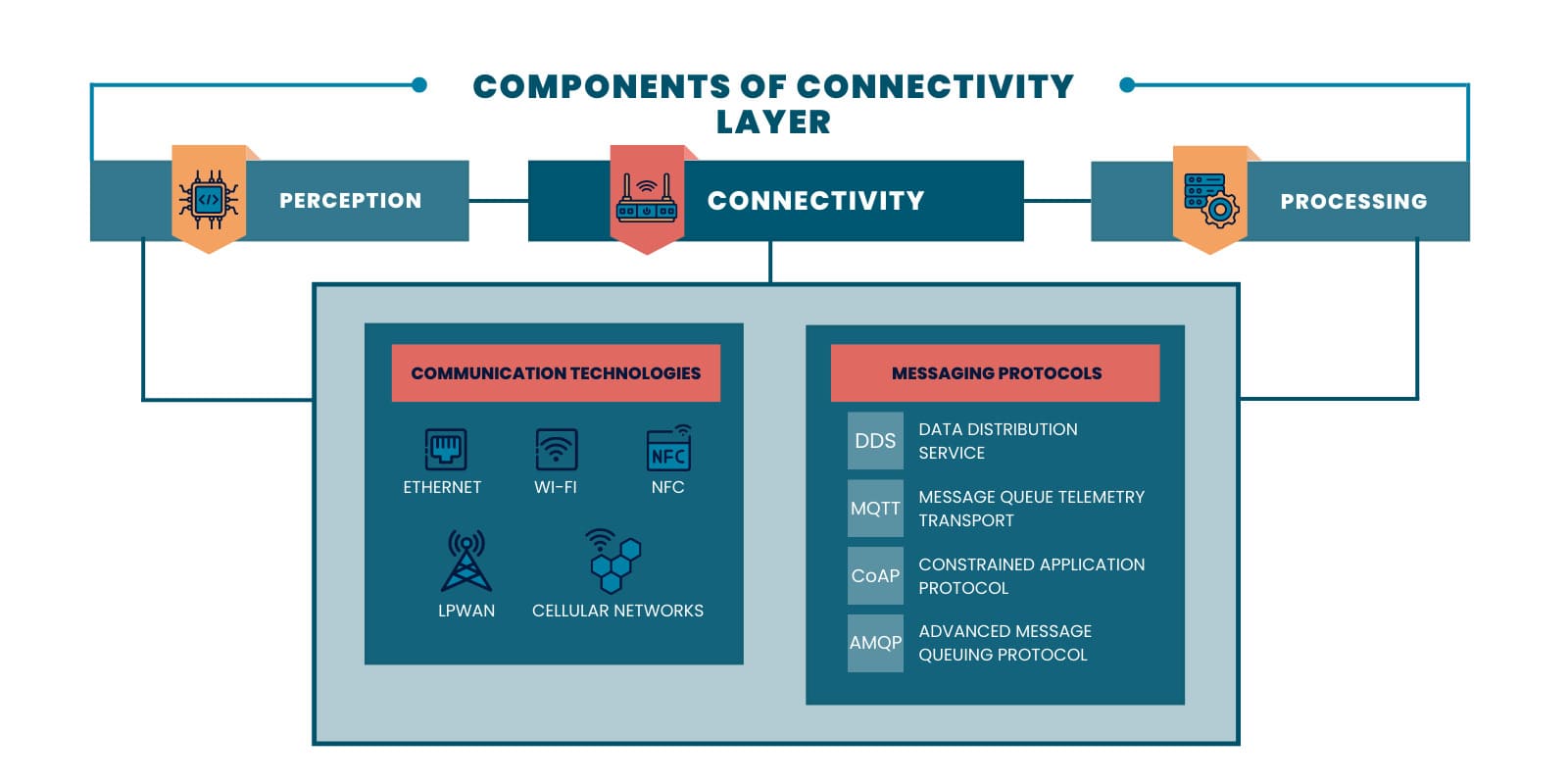
The connectivity layer handles the communication between devices, networks, and cloud-based systems required by the architecture of IoT solutions. Connections between the perception layer and processing layer are established with a TCP/IP or UPD/IP stack. It can also be implemented using gateways that convert signals to different protocols. Gateways can also perform encryption and decryption of data transmitted through the IoT system.
Multiple communication technologies are used when constructing the connectivity layer of a solution’s IoT architecture. The communication technology chosen for a given IoT implementation is often dependent on the design of the system. Device type, the distance the signals must travel, and potential obstructions all are considered when devising the connectivity layer.
Following are some of the communication technologies deployed in the connectivity layer of IoT architecture.
- • Ethernet – This technology uses wires to provide secure and high-speed connectivity over short distances.
- • WiFi – WiFi provides high-speed connectivity wirelessly over short distances.
- • Near Field Communication (NFC) – This is a highly-secure method of sharing information between two devices that are located within four inches of each other with minimal power consumption.
- • Low-power Wide-area Network (LPWAN) – LPWAN is a technology created for IoT devices that provides low power consumption, extended battery life, and long-range wireless connectivity.
- • Cellular networks – Using cellular networks gives an IoT architecture fast and reliable connectivity with almost global coverage. It is expensive and exhibits high power consumption.
Multiple messaging protocols are used to share data among devices and with cloud platforms including:
- • Data Distribution Service (DDS) – Connects IoT components in real time;
- • Message Queue Telemetry Transport (MQTT) – Used for collecting data from low-powered devices;
- • Constrained Application Protocol (CoAP) – For use in devices with constrained memory or power resources;
- • Advanced Message Queuing Protocol (AMQP) – Supports data exchange between servers.
The right combination of communication technologies and messaging protocols is essential for creating an IoT architecture that best addresses the project requirements.
Processing
The processing layer is where data generated in the perception layer and transmitted by the connectivity layer is collected, stored, and processed. Data passes through two critical stages in the processing layer.
The data accumulation stage – This stage provides the mechanism to transform generated data into a form usable by the application layer. The purpose of this stage is to efficiently sort and store the accumulated data, making it accessible for further processing in the application layer. Data is stored differently or may be discarded based on its relevancy to the IoT system. Multiple storage technologies and methodologies are used to store IoT data.
The data abstraction stage – This is the final stage of data preparation where information is formatted and abstracted for use in applications. Data from both IoT and non-IoT sources are consolidated and multiple formats are synchronized. Information is aggregated and stored centrally so it can be accessed efficiently.
The processing layer also handles reformatting data returned from the application layer so it can be understood by endpoint devices. These stages hide hardware details and allow teams to focus on solving business problems.
Application
The application layer of IoT infrastructure is where data is analyzed to solve business problems or meet objectives. Software tools convert data from the processing layer into meaningful information for users or automated processes. Application programming interfaces (APIs) are used to integrate IoT software with middleware. Some IoT platforms offer built-in software development capabilities that provide features such as data visualization and analytics.
Users interact directly with the application layer and can monitor IoT devices and observe data through various tools like dashboards and mobile apps. Software tools also make use of data in the application layer to perform a wide range of activities. Following are just a few of the ways the application layer is used in business and industry.
- • The GPS in your smartphone that helps you avoid getting lost is an example of a consumer-focused IoT application.
- • Systems provide business intelligence regarding consumer activity and purchasing trends to facilitate corporate decision-making.
- • Robots and automated equipment are monitored and controlled by the application layer. Systems can demonstrate improved performance and accuracy over time using machine learning technology.
- • Intelligent traffic control systems rely on the application layer of the IoT architecture to provide reliable and timely information.
Additional IoT Architecture Layers
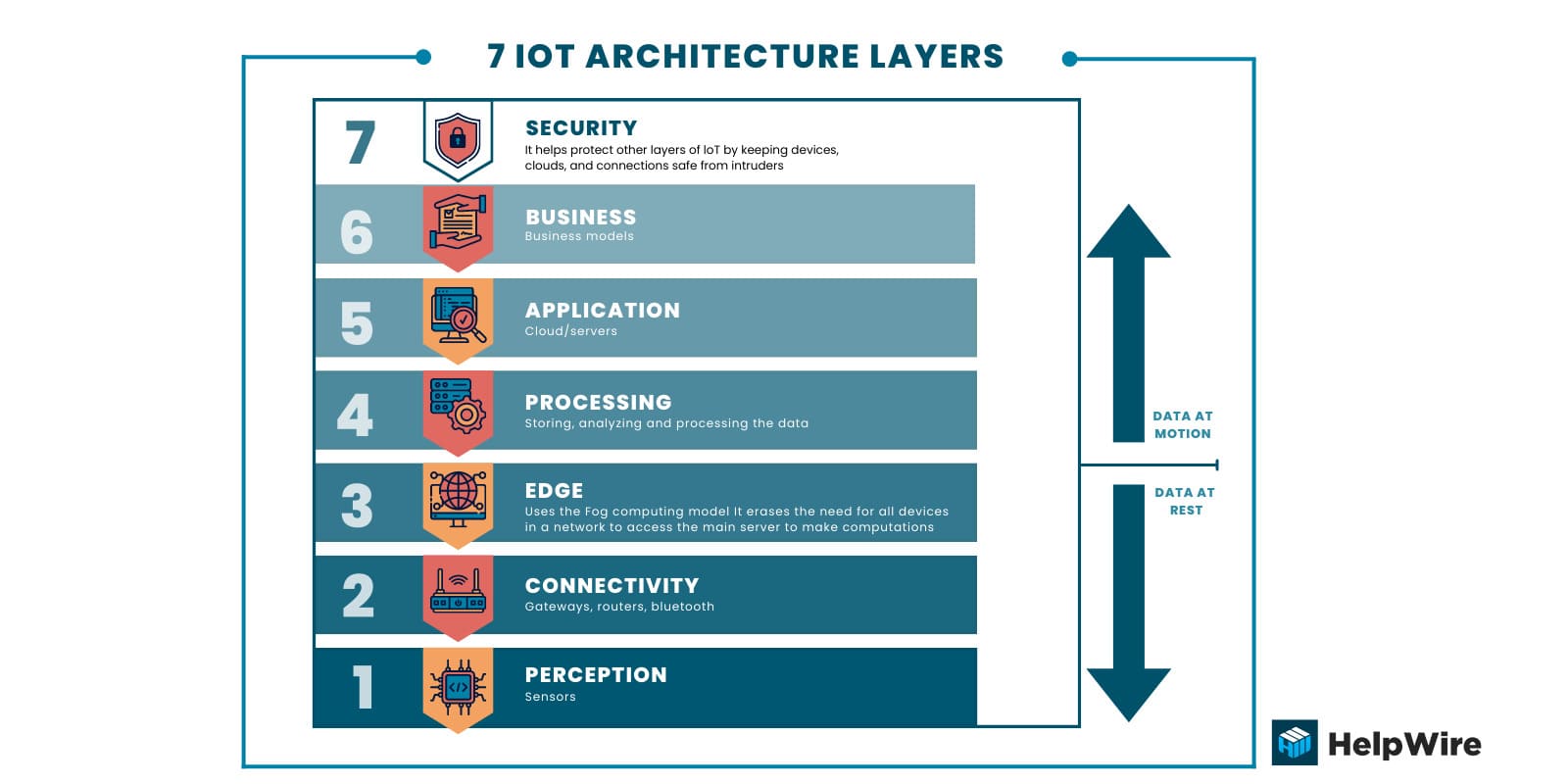
Additional IoT architecture layers are used to more precisely define the purpose of the main layers and to improve the performance of the overall IoT infrastructure. Let’s look at three additional layers you may encounter when discussing IoT layered architecture.
Edge or fog computing
The fog computing layer, or edge computing, is designed to reduce latency and take advantage of the features available in 5G mobile networks. The goal is to process and store information as close to its source as possible without transmitting it to a cloud platform. These activities are performed at the edge of the network to save time and conserve the resources required to communicate with the cloud.
Edge computing enables large volumes of data to be processed in real time. In some cases, the edge layer plays the role of the processing and application layers, allowing data to be directly returned to actuators and devices. The edge also can perform analytics and evaluate if data needs further processing or should be sent to another location.
Business
The business layer is where data-driven solutions and decisions are extracted from the application layer. It may be comprised of multiple instances of the application layer, making it more complex and deserving of a separate designation. Companies investing in IoT solutions are primarily concerned with the business layer of IoT infrastructure.
Security
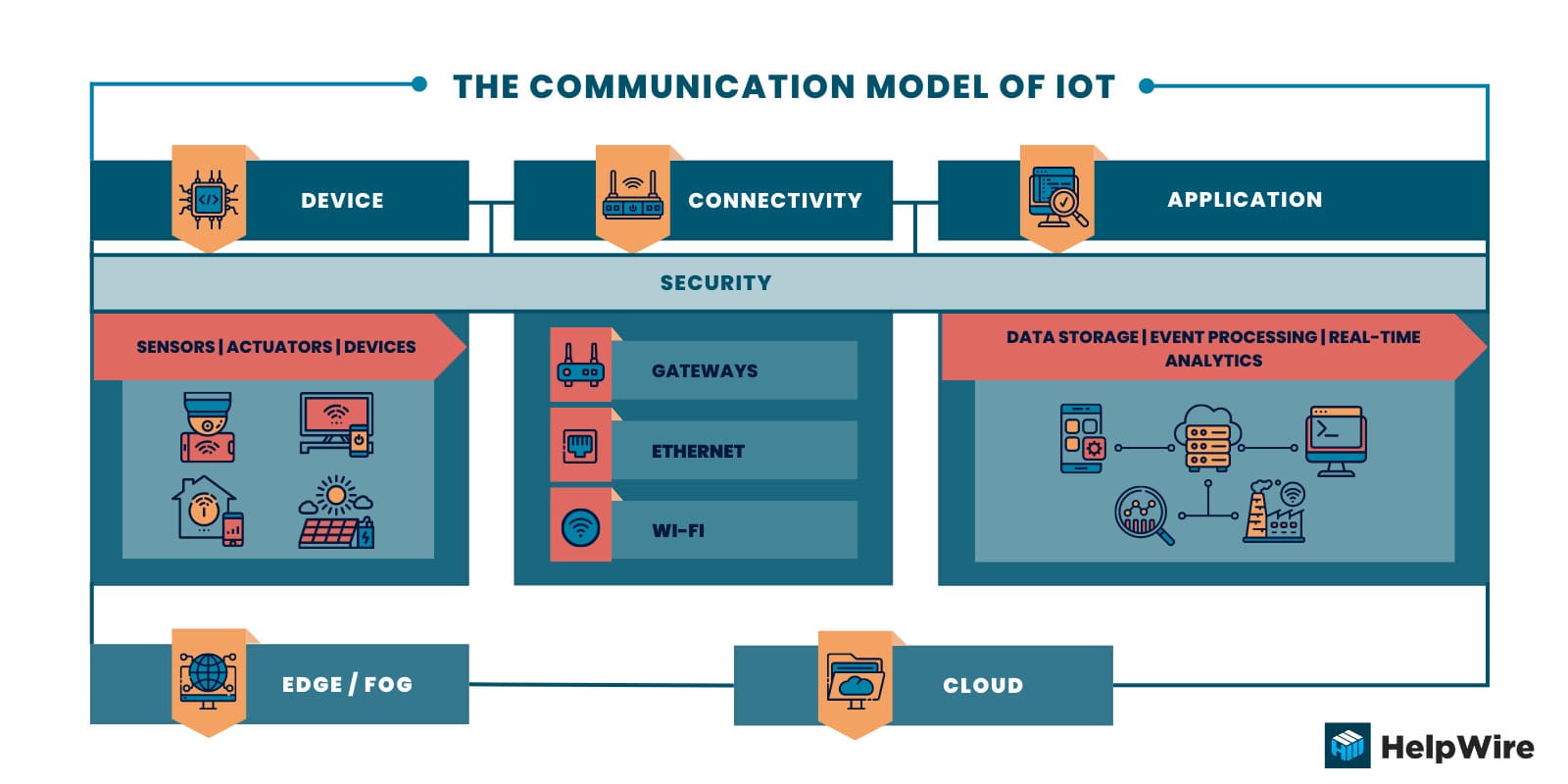
End-to-end security is essential in an IoT infrastructure. Sensitive data is often exchanged in an IoT system. Critical municipal infrastructure components such as power generation rely on the security of IoT architecture. Compromised IoT-connected devices can cause great danger to public health and safety. The security layer extends throughout all IoT architecture layers and is critical to the success of an IoT solution.
Security can be broadly classified into three categories.
Device security – Security begins at the perception layer with devices equipped with hardware and firmware safeguards. Some specific elements of device security are:
- • Ensuring proper authentication through cryptographic keys;
- • Physically protecting devices with hardened exteriors;
- • Preventing unauthorized code to run on a connected device;
- • Installing firmware and security patches to address vulnerabilities.
Connection security – Data needs to be secured by encrypting it when in use by the connectivity layer. End-to-end encryption eliminates the risk of data being intercepted and misused by unauthorized users.
Cloud security – Cloud security involves encrypting stored data to reduce the risk of data breaches involving sensitive information. Access to IoT applications needs to be limited with strong authorization and authentication measures. Devices also need to be authorized when connecting to the cloud or the IoT system to guard against rogue devices.
Security should be of primary concern in all IoT implementations. The complexity and flexibility possible with IoT solutions can make them challenging to secure. These security challenges must be overcome when developing an IoT system.
Conclusion
The layered IoT infrastructure enables business decisions to be driven by data generated from distantly located sensors and devices. Each layer has a distinct role in the functionality of the system and can be configured to meet a company’s business objectives. The immense flexibility in the types of devices, technologies, and different standards and protocols used to construct an IoT architecture provides virtually limitless possibilities for IoT implementations.
Major cloud providers have come on board and offer packages of services tailored to a company’s IoT environment. These include analytical engines powered by artificial intelligence and machine learning to help decision-makers optimize the information available from IoT solutions. Data is encrypted in the cloud and access control and authentication can be enforced to meet business requirements.
The architecture of IoT systems allows for continuous innovation at each layer to optimize how data is collected and used. As the technology matures even further, the IoT will be involved in more of your daily activities. Understanding its layered architecture may help you if faced with issues or anomalies when interacting with IoT systems.