IoT Security — Challenges & How To Overcome Them
With the variety of IoT hardware and devices on the market, it’s only natural to struggle with the numerous IoT (Internet of things) security vulnerabilities and challenges. With the ability to establish an internet connection, and interact in this online landscape via the collection and transfer of information/data, users are naturally exposed to IoT security issues.
While the varied assortment of IoT allows users to enjoy numerous devices, it’s a major reason why IoT fragmentation carries a plethora of IoT security concerns.
An absence of forethought and technological standards in the IoT industry made space for compatibility issues that further complicate security measures.
An additional challenge has to do with the portability of IoT devices. Their mobile nature provides an innate possibility of threats that spread to more than a single network.
Compounding these concerns are even more factors that IoT security must address.
This article is about basic IoT security and provides insight that will help readers better understand why it’s so important to ensure maximum IoT device security in the modern world.
What is IoT security?
Internet of things (IoT) security is the procedure of securing IoT devices, as well as the network they are connected to. IoT cyber security’s primary goals are establishing and ensuring user privacy and data confidentiality. It provides not just device security, but the integrity of the whole IoT infrastructure.
IoT security is quite a broad topic — but extremely important to understand. When IoT security standards are executed properly, the IoT ecosystem can function safely and effectively.
The field of IoT includes adding internet connectivity to devices executing specific functions. Unfortunately, with every device that gets connected, the threat of attack grows as cyber actors scan through network-connected devices in an attempt to exploit known weaknesses.
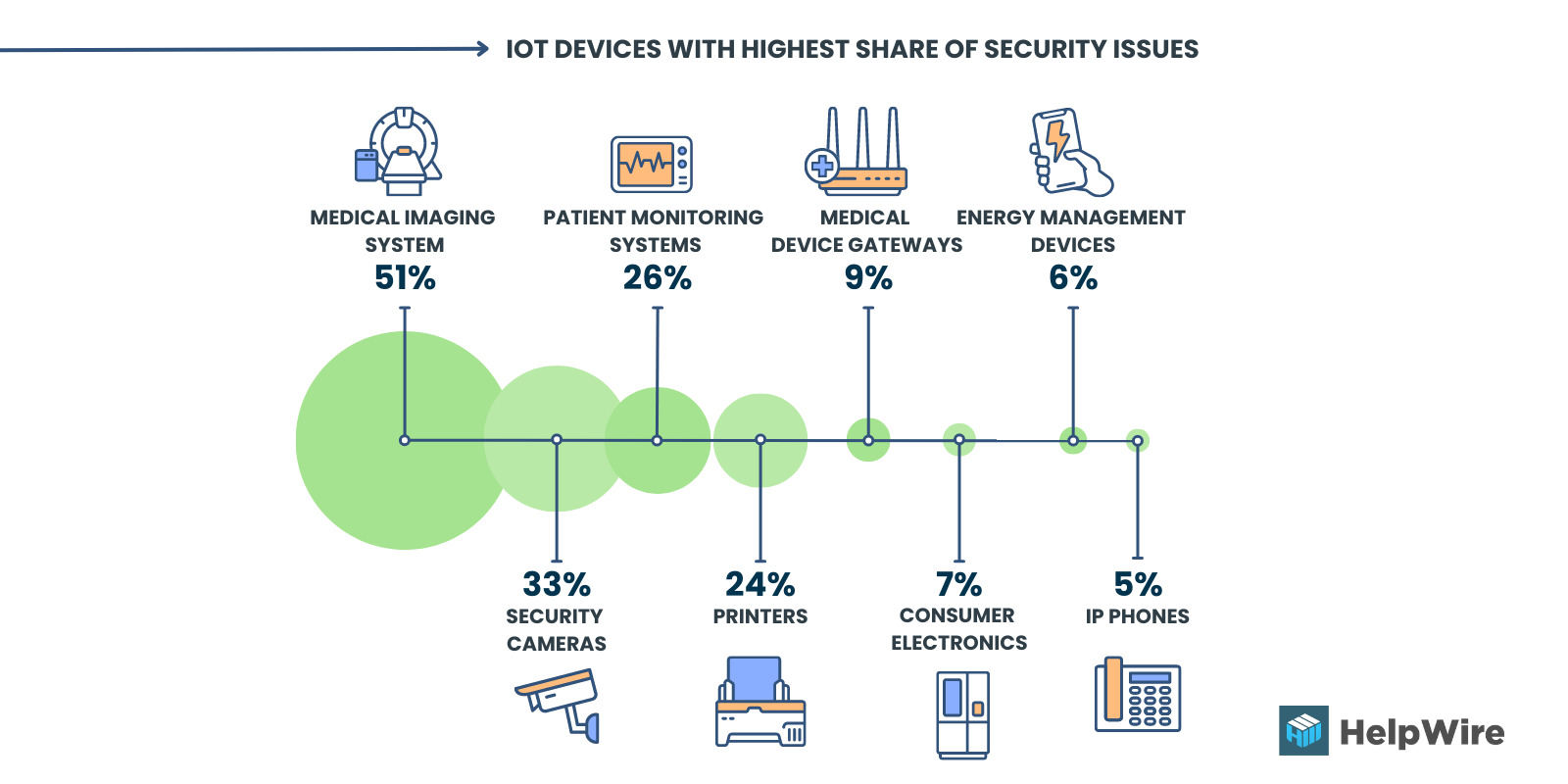
Image 1. IoT devices with the highest share of security issues¹
IoT is quite an enticing target for cybercriminals because:
- • It’s an endless bounty of data;
- • It’s relied upon for essential functions by so many individuals;
- • It’s implemented/integral to highly-important industries.
IoT already deals with attacks and vulnerabilities such as distributed denial of service (DDoS), data breaches, and malware infections. These IoT security risks demonstrate the necessity for powerful and reliable IoT security solutions.
And such IoT network security solutions must adapt rapidly with each passing day, as the strategies and tools that counter IoT security measures continue to improve.
Types of IoT security
A robust IoT security system is both technically appropriate and economically sustainable. Building an IoT strategy without adequate security measures is more akin to a hopeful desire than an actual security strategy.
Persistent and unresolved IoT security issues negatively affect public trust and may lead to increased legislative oversight (both conditions slow the adoption of IoT in other industries).
Here, we list the main types of standard IoT security.
- • Using a Bootstrap server to develop secure onboarding.
- • Implementing single-factor and multi-factor device authentication systems.
- • Integrating secure internal and external APIs (platform side).
- • Enforcing a consistent device authorization process.
- • Practicing data encryption to prevent unauthorized access.
- • Providing secure public keys or certificates for all levels.
- • Providing secure elements to store, encrypt, and decipher.
- • Integrating a predictive device and platform-side security system.
- • Developing safe and consistent remote over-the-air firmware/software updates.
IoT security importance
While enterprise-level IT teams defend their standard IT devices with appropriate network security, the risks associated with IoT devices aren’t as widely understood — and this can mean that securing them often gets overlooked.
The reasons for this are many, but we’ll highlight the main three:
Reason 1: Standard cybersecurity systems can’t recognize specific types of IoT devices, their unique danger profiles, or their associated behaviors.
Reason 2: Few organizations have an accurate asset inventory of their IoT devices in their security solutions. As a result, IoT devices are not properly incorporated into an IT infrastructure, and they bypass standard IT security processes/controls like security patching, asset management, and so on.
As shown in Figure 1, only 29 percent of respondents in the study conducted by Ponemon Institute say their organizations have a complete inventory of their IoT devices.
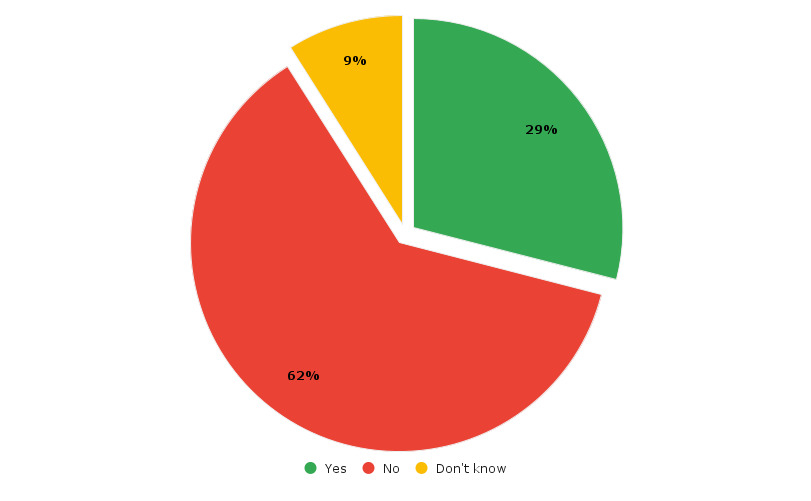
Image 2. Percentage of organizations having a complete inventory of their IoT devices²
Reason 3: Various IoT devices in the network use different hardware and firmware, chipsets, and operating systems. This further complicates their unification into an integral IoT security system.
When robust security is lacking, all IoT devices in the network are vulnerable to security breaches, getting compromised and accessed by bad actors who intend to steal user data and put systems offline.
Network security and operations teams must integrate reliable and powerful IoT security as part of their standard procedures so that unmanaged devices get the same level of monitoring and control as more commonly managed devices.
The most common IoT security issues
IoT security risks include some of the most common attack tactics thought obsolete by modern standards. However, there are two new attack tactics that become more widespread: P2P command-and-control communication and self-propagating IoT malware worms. Both tactics target decades-old legacy OT protocols to disrupt critical business operations in the enterprise.
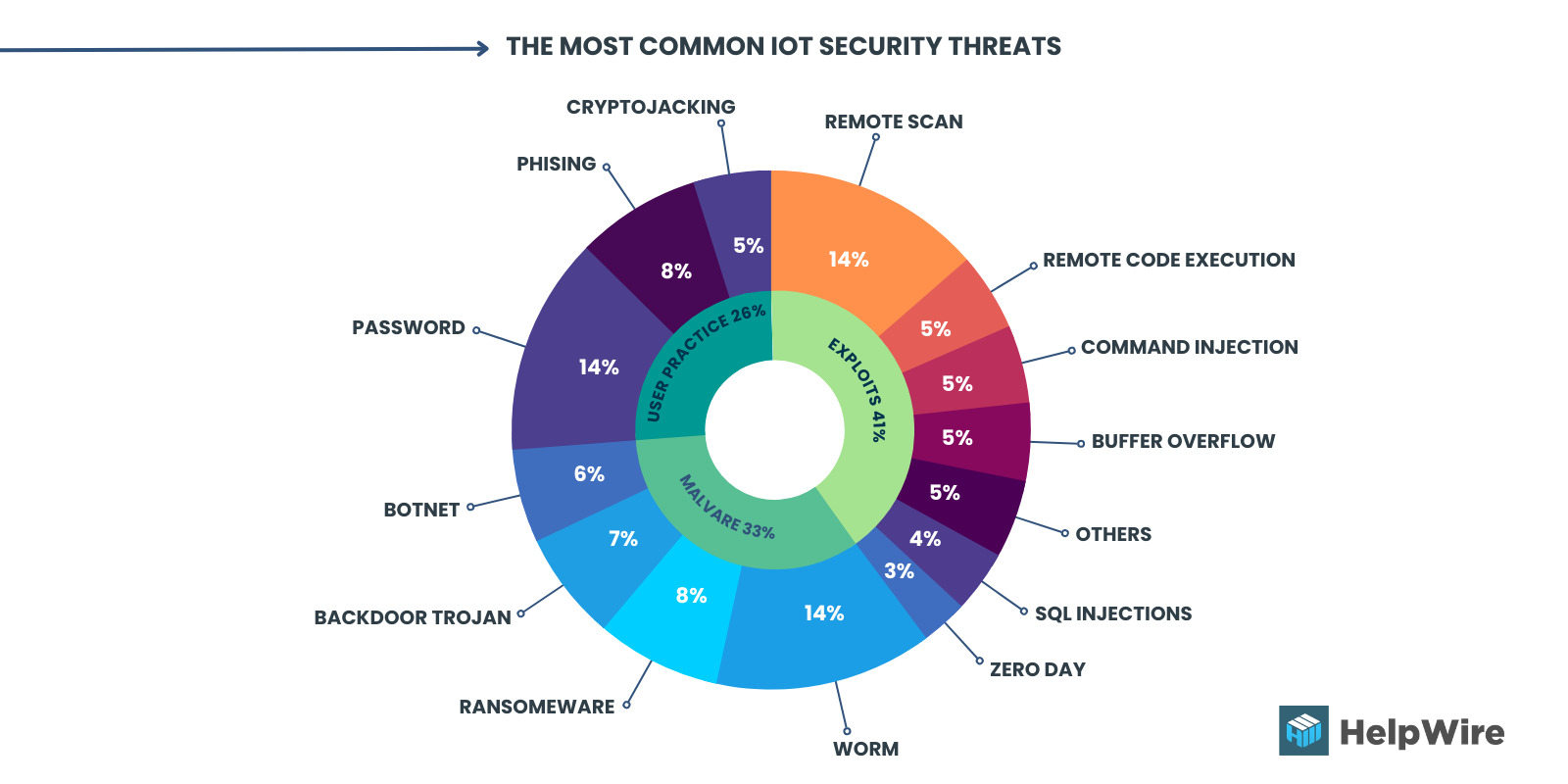
Image 3. The most common IoT security threats¹
Let us review four key IoT security challenges in the modern digital world.
Challenge 1: Outside breaches
A reason for worry regarding securing the IoT is that as more and more diverse types of IoT devices connect to the network, the attack surface expands dramatically.
Adding to this, the whole network security is mitigated to the level of integrity and protection provided to the least secure device — unless that device has already been effectively secured. Similarly, practically all traffic involving IoT devices isn’t encrypted. This, obviously, means that confidential data is at huge risk of attack.
In a network, endpoints are the devices connected to the internet, and this encompasses the IoT devices. Each endpoint offers a potential entry point for cybercriminals or bad actors to expose a network to risks from the outside. Thus, similar to alternative endpoints, IoT devices are susceptible to extreme weaponization.
When infected with malware, IoT devices can then be utilized as botnets that launch distributed denial-of-service (DDoS) attacks on the network cyber criminals seek to dismantle.
Challenge 2: Security vulnerabilities
The massive issues of vulnerability incessantly plague large-scale organizations and individual users alike.
One major reason IoT devices are at risk is due to their lack of computational capacity for built-in security.
Additionally, such vulnerabilities are so widespread because of the limited budget for developing and testing secure IoT firmware — which is influenced by the price point of a device, and its very short development cycle.
Apart from the devices themselves, security risks in web applications and related IoT device software have the potential to compromise the whole system. Malware operators keep their eyes peeled for such opportunities, and remain familiar and knowledgeable — even when considering older/outdated security vulnerabilities.
Challenge 3: Substandard password practices
Improper password security practices constantly trigger password-related IoT device attacks. Additionally, weak device and network security postures mean that IoT devices are incredibly easy targets. Unfortunately, the rate at which IoT devices are left unpatched and running outdated operating systems continues to grow.
Several of the most frequent IoT device attacks are exploits done using processes like network scanning, command injection, remote code execution, etc. Nearly half of the attacks strictly focus on exploiting device vulnerabilities, as IT-focused attacks scan network-connected devices seeking to exploit known security gaps.
Challenge 4: Malware infection
Despite the restricted computing capacity most IoT devices deal with, they’re still susceptible to malware infection. This is a fact that cybercriminals have relied upon to great efficacy over the past few years.
IoT botnet malware is among the most commonly seen variations because they’re profitable and versatile for cybercriminals.
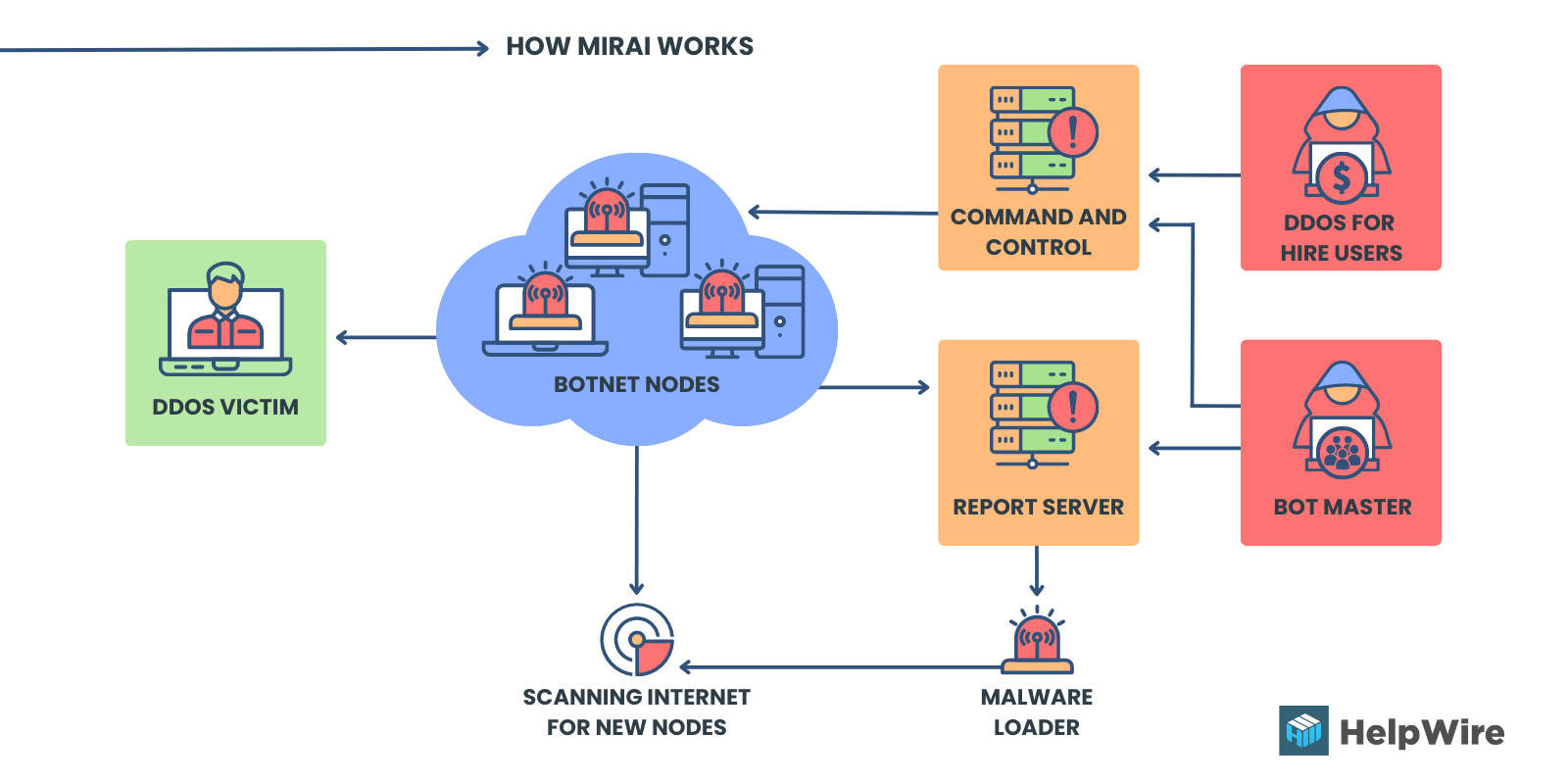
Image 4. How Mirai botnet works
The most notable cyberattack took place in 2016 when Mirai dismantled major services and websites utilizing many common IoT devices. Alternative malware types include ransomware and cryptocurrency mining malware.
How to secure IoT devices
No instant fix is available to resolve the IoT security issues described in this article. Specific strategies and tools may be required to effectively secure specialized systems and the IoT element. However, users can implement multiple best practices that reduce risks and help prevent IoT security threats.
The lifecycle framework includes 5 essential stages for securing IoT devices.
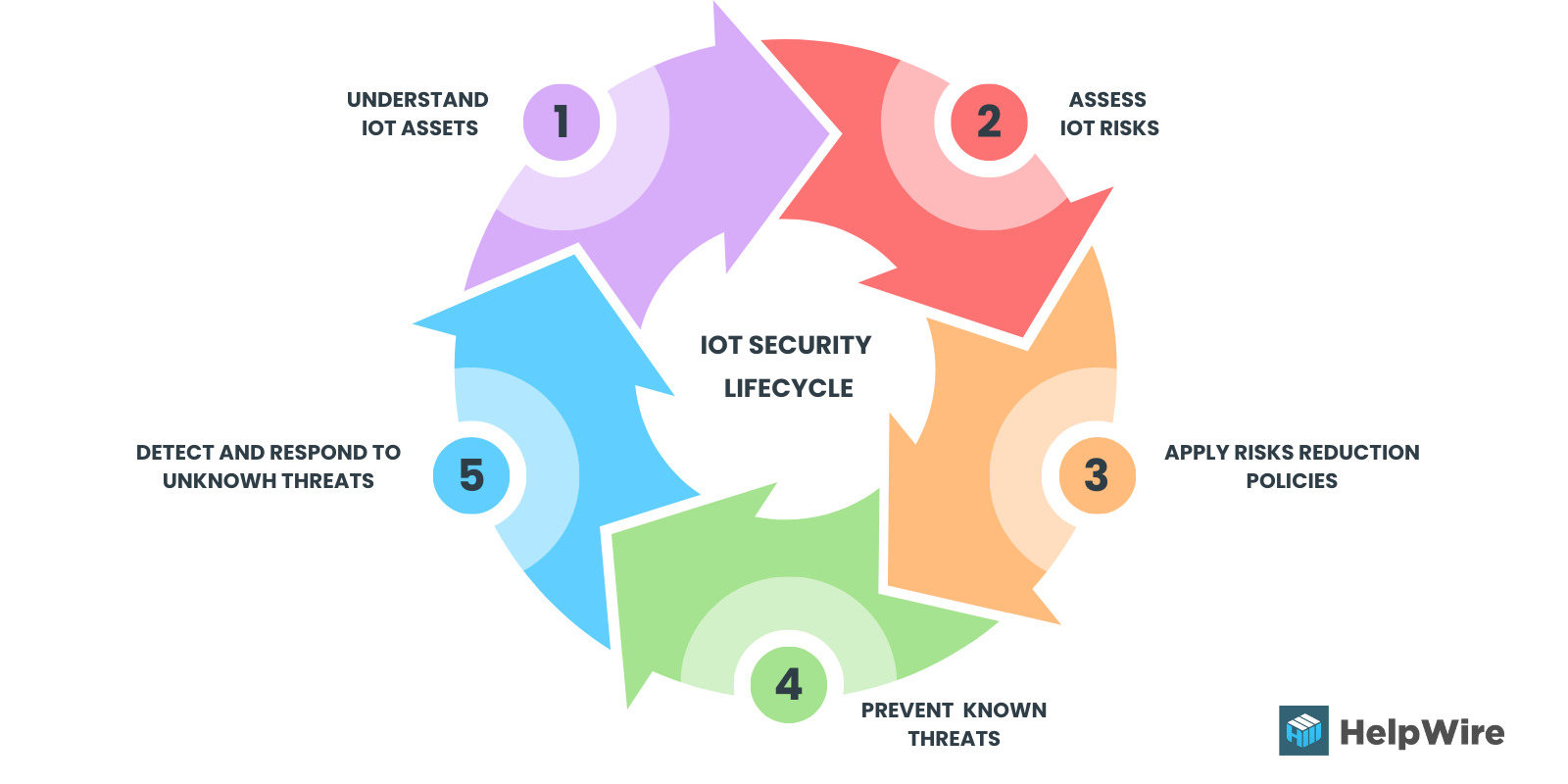
Image 5. IoT security lifecycle¹
To ensure a secure connection between IoT devices, operation and network security teams must build standard processes that ensure all IoT devices fall within the same level of visibility and control. The IoT security lifecycle approach involves network operators enforcing five critical stages of security checks.
- The first step is for network operators to identify all managed and unmanaged devices.
- Next, assess and identify any vulnerabilities that affect the integrity of the IoT devices.
- After assessing all risks, the team creates, automates, and enforces a zero-trust policy.
- Prevent known threats by building and integrating preventive measures into the system.
- The final stage is to develop and deploy quick responses to unknown threats that may affect IoT devices and networks.
Here are some examples of more practical activities for securing IoT infrastructure.
You can assign an overarching “administrator of things”. Instilling one person as an IoT device and network administrator can help mitigate oversights in security protocols. This administrator is put in charge of prioritizing IoT device security 24/7 — even while at home.
Uncover and record every IoT device in the network. You can’t defend what can’t be seen. Profiling all IoT devices allow an IT security team the necessary insight into the unmanaged assets within the IoT environment (i.e., the precise number of network-connected IoT devices, their underlying OS, risk profiles, and behavior while interacting with alternative connected devices).
Routinely check for updates and patches. Security risks are large and incessant problems in the IoT field because vulnerabilities could come from any layer of IoT devices. Cybercriminals can still take advantage of even older security issues to infect devices. This showcases just how long unpatched devices can remain online.
Implement powerful password protection for all accounts. Highly-optimized passwords can halt numerous cyberattack opportunities. To better manage complex passwords, password management tools help users create unique passwords, and then store it securely in the app — or within the software itself.
Place special prioritization on Wi-Fi security. Many methods users have at their disposal include: enabling router firewalls, disabling WPS and enabling the WPA2 security protocol, and implementing a secure password to access the Wi-Fi. Making sure the router settings are secure also plays a large role in this strategy.
Remotely monitor IoT devices’ behavior and network baselines. It can be hard to detect cyberattacks, but knowing device and network baseline behaviors (such as typical bandwidth, speed, etc.) enables users to more easily recognize deviations that could indicate malware infections.
Implement network segmentation. Users can reduce IoT-related attack threats by developing an independent network for IoT devices, and yet another for guest connections. Network segmentation could also help defend against attacks, and isolate potentially problematic devices that can’t get taken offline immediately.
The possible consequences of IoT attacks
Apart from IoT security challenges themselves, the consequences (in the context of the IoT) can cause more damage. IoT offers a unique ability to affect both physical and virtual systems.
Cyberattacks committed against IoT ecosystems have the potential for far less predictable implications since they more easily translate into physical repercussions.
This is most noticeable in the industrial internet of things (IIoT field) — an area where past cyberattacks have already highlighted cascading consequences.
Regarding the healthcare industry, IoT devices are already utilized for remote monitoring of patients — proving to be extremely helpful throughout the pandemic. Attacks on those devices put sensitive patient information at risk — or could even endanger a patient’s health and safety.
Uncomfortably, compromised smart home devices could let cybercriminals monitor someone’s household, jeopardize security devices (like a smart lock), and even turn devices against their owners. This was, in fact, the case when baby monitors or smart thermostats are hacked in separate attacks.
Notable IoT security breaches and IoT hacks
From stories about hackers using television and refrigerators to spam users to hijacking baby monitors and speaking to children, numerous malware attacks have made headlines in the recent decade.
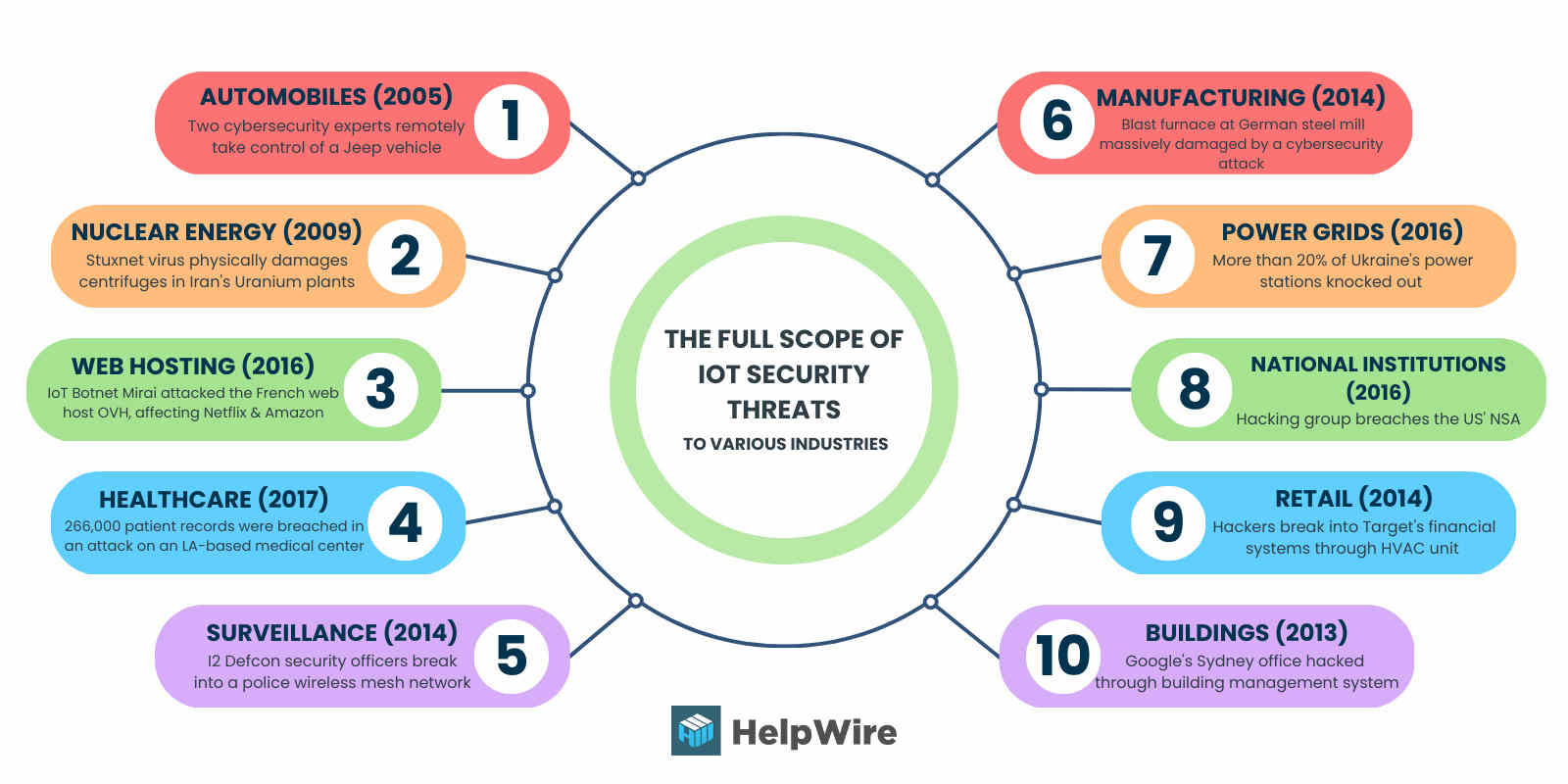
Image 6. The full scope of IoT security threats
A prominent example was the 2006 Operation Olympic Games cyber attack on Iran. Research revealed that the United States and Israel developed Stuxnet, a digital worm, to destroy Iran’s uranium centrifuges. The cyberweapon uses malware to target supervisory control and data acquisition (SCADA) systems in industrial control systems (ICS), infecting instructions sent by programmable logic controllers (PLCs). This cyber attack is often considered one of the earliest examples of IoT attacks.
In 2013, a researcher at Proofpoint discovered the first IoT botnet. According to a study conducted by the security firm, over 20 percent of the botnet consisted of household smart appliances other than computers. These findings revealed that internet criminals have begun hacking smart kitchen appliances and other IoT devices for ulterior motives.
In 2015, Chrysler recalled over one million vehicles after security researchers Charlie Miller and Chris Valasek wirelessly hacked the Jeep’s digital systems. Using a port under the Jeep’s dashboard, they could wirelessly connect to the vehicle’s CAN network, Uconnect. As a result, they could change the radio station, stop the accelerator, and remotely turn on the air conditioner and windshield wiper.
In January 2017, the Food and Drug Administration issued a notice to St. Jude, warning them about the vulnerability of the hospital’s radio frequency-enabled implants (physicians used these implants to prevent heart attacks and monitor patients’ heart function). Hackers could access the transmitter that reads and shares patients’ data remotely. These implants included defibrillators, resynchronization devices, and pacemakers.
In March 2021, over 1000 Verkada cameras suffered a massive breach of privacy from a group of swiss hackers. The Silicon Valley startup provided cloud-based camera security services to its customers. Unfortunately, many hacked cameras monitored sensitive institutions like prisons, schools, and hospitals.
Another notable example is the role of malicious cyber activity in international conflict. For example, during the Russia/Ukraine war, nation-state actors were actively involved in cyber campaigns against Ukraine using malware like BlackEnergy and NotPetya to significantly disrupt critical sectors.
IoT security standards and regulations
As IoT security concerns gain traction, a new problem is emerging. The challenge facing the industry today appears two-fold: which regulations apply to the industry and is compliance with IoT regulations enough to guarantee adequate security?
As IoT regulatory standards and requirements change with geography, complex factors that affect design, manufacturing, and implementation must be considered. Although standard organizations provide core requirements for IoT security worldwide, many governments are considering stricter regulatory approaches.
A prominent example of this shift is the IoT Cybersecurity Improvement Act that the US Congress introduced in August 2017. This act required that any IoT device sold to the US government would not have known vulnerabilities, not use default passwords, and offer mechanisms to patch the device.
By the end of 2020, the president signed the improvement act, directing the National Institute of Standards and Technology to develop minimum cybersecurity standards for any IoT devices the US government owns or controls.
The General Data Protection Regulation (GDPR) released in May 2018 unites all laws concerning data privacy in the European Union. These privacy laws also cover IoT devices and their networks.
Fast forward to February 2019, the European Telecommunications Standards Institute released the first standard for consumer IoT security to promote better security practices. These new standards were created to drive the adoption of a security-by-design principle when developing new consumer products. The new provision contains 13 provisions to ensure a robust security system for consumer IoT devices.
Summing up
IoT security solutions differ pending upon someone’s specific IoT application and their place within an IoT ecosystem. As one example, IoT manufacturers (from product makers to semiconductor companies) would do well to focus on constructing security from the very beginning:
- • Staying up-to-date with security upgrades;
- • Ensuring hardware is tamperproof;
- • Creating secure hardware;
- • Applying firmware updates/patches;
- • Initiating dynamic testing.
One solution that developers should prioritize is securing integration and software development. Hardware security and authentication are crucial protection measures for anyone implementing IoT systems.
Similarly, it’s key for operators to keep systems up to date, reduce malware, audit, defend infrastructure, and protect credentials. However, as with any IoT deployment, one must calculate the cost of security vs. any risks before implementation.
Frequently Asked Questions
What are the different types of IoT security?
Why is IoT security important?
What are the main types of IoT security threats?
References
- According to the 2020 Unit 42 IoT Threat Report.
- Based on the Ponemon Institute study The State of IoT/OT Cybersecurity in the Enterprise.