Best Practices to Access IoT Devices Behind Firewall
Using a firewall to protect Internet of Things (IoT) systems will stop illegal access. Port forwarding, VPN, and SSH are some methods to access them. Continue reading to know more about these methods and their peculiarities.
How to Access IoT Device Behind a Firewall
Home networks are common for IoT devices, and firewall and secure router configurations can help protect these devices from unauthorized access.
However, there are instances when you need to access an IoT device behind firewall.
Port Forwarding
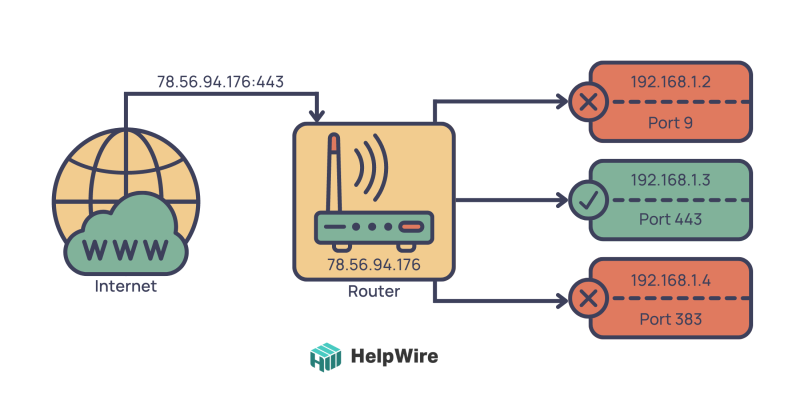
With this method, you may divert inbound data from a specific router port to IoT device ports. It’s comparable to asking the gatekeeper to let an individual in so they may visit you in your room.
Port forwarding does, however, provide specific security hazards. For example, inadvertently connecting your IoT gadget to the internet might open it to assaults. Thus, using strong passwords and maintaining your router and IoT devices updated with the most recent security updates is crucial.
The proxy desktop protocol is an alternative method for accessing an IoT device protected by a firewall. RDP enables users to connect to a remote desktop via a network. This may help manage and control IoT behind firewall.
To manage IoT behind firewall and interact with the internet while disguising their IP addresses, NAT device may also safeguard IoT appliances. Filtering traffic and obstructing illegal access, proxies, and packet-filtering can safeguard IoT devices.
WebSockets is another nifty technology that binds IoT connectivity. This system allows real-time communication while streaming data. It does this process by connecting servers and web browsers in real time.
Virtual Private Network (VPN) Set Up
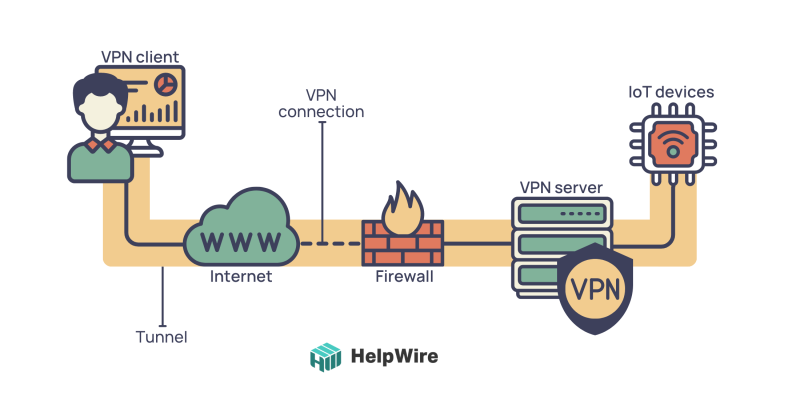
Virtual Private network or VPN allows users to connect IoT device behind firewall over the Internet through protected network.
Virtual Network Computing (VNC) is another method of controlling IoT devices defended by a firewall. Using another computer or mobile device, you may use this to see and manage a remote desktop.
Edge computing is another important technology in IoT networking. It entails processing data more closely with the endpoint device, lowering the volume of data that must be transferred over the internet, and speeding up response times.
You can also send commands to the IoT device behind the firewall using specialized software that enables IoT remote access, such as TeamViewer or LogMeIn. These technologies give you a safe way to manage your IoT devices from any global location remotely.
Secure Shell Protocol (SSH)
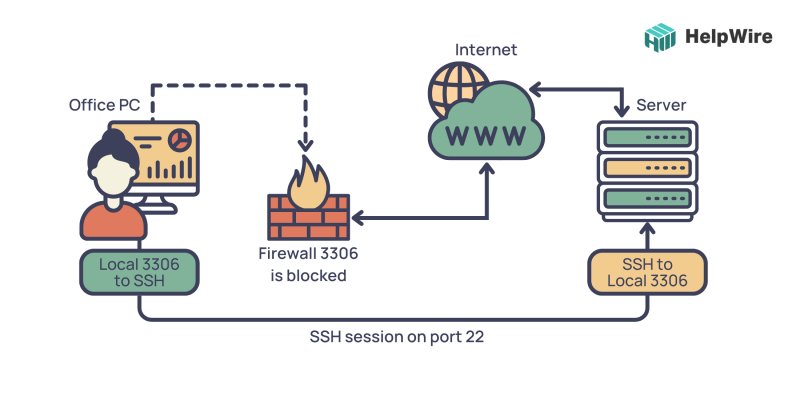
Command-line access and remote administration of your IoT device are made possible through the Secure Shell, or SSH, technology. It’s similar to controlling your IoT gadget from a distance with a magic wand. SSH enables remote command execution from the command-line interface of an IoT device.
You may issue commands to your IoT device after connecting to it using SSH, such as turning on or off smart lighting in your smart home or seeing your sensor data.
SSH encrypts the communication and blocks illegal access, making it safe to access your IoT devices protected by a firewall. It’s also a lightweight technique that doesn’t require much bandwidth or computing power, making it suitable for low-power IoT devices.
It might be challenging to monitor IoT devices blocked by a firewall. But there are options out there that can support you in completing this work. For instance, SNMP (Simple Network Management Protocol) may monitor IoT behind firewall functionality and status remotely.
Apart from the methods discussed earlier, advanced techniques can be employed to access and manage IoT devices behind firewall. These methods provide remote access and offer enhanced security features, ensuring the safe and efficient operation of IoT devices.
Many protocols, such as MQTT (Message Queuing Telemetry Transport) and CoAP (Constrained Application Protocol), can send orders to an IoT device protected by a firewall . These IoT protocols enable the safe transfer of instructions and data to IoT devices protected by firewall.
Remote SSH IoT behind firewall involves using an SSH tunnel to bypass firewall restrictions and gain secure access to the IoT device. This technique allows you to execute commands remotely while maintaining your device’s and network’s security.
Meanwhile, IoT RDP behind a firewall involves setting up an RDP connection to an IoT device, allowing you to manage and control the device remotely. Using this approach, you may interact with graphical interfaced devices as though you were standing right before them, which is advantageous.
Utilize specialized monitoring tools and protocols like SNMP or MQTT to monitor IoT devices protected by a firewall.
Connecting IoT vnc behind the firewall lets you view and control a device’s desktop remotely. This method provides secure access to the device’s interface, allowing you to effectively perform management tasks and troubleshoot issues.
To send command IoT device behind firewall, use secure communication protocols like CoAP. This interface makes it possible to securely send instructions and data to IoT devices that are firewall-protected, making sure that only authorized users may communicate with the devices.
These advanced techniques provide additional options for accessing and managing IoT devices behind firewall. You can keep control of your IoT devices while protecting the security and privacy of your network by using these techniques.
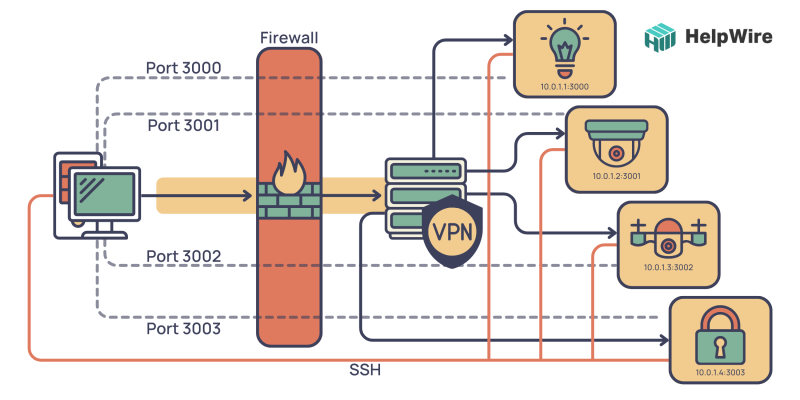
What is IoT Firewall? How Does it Work?
An IoT firewall is a security system that protects IoT devices and networks from cyber threats. Its primary purpose is to prevent unauthorized access to IoT behind firewall and networks.
IoT firewall checks the traffic from your devices and only allows authorized traffic to pass through.
Your devices are shielded against online threats and illegal access by a firewall, which stands between them and the internet.
The IoT firewall analyzes the network traffic and applies rules to decide whether to allow or stop it. The firewall will, for instance, determine if a device’s attempt to connect to the internet is approved. If so, the connection is valid. The connectivity is blocked if it’s not.
IoT firewall can be hardware- or software-based. A software-based firewall is a program that safeguards a computer or router by running on such devices.
These firewall come in various types, each with unique features and capabilities. For example, some can encrypt communication to safeguard your data, while other firewall can identify and prevent dangerous traffic.
Why is IoT Security Important?
IoT devices are now widespread in homes, businesses, and schools, streamlining essential tasks and boosting efficiency. However, with their growing use, it is crucial to implement security measures to protect private and sensitive data.
IoT security is crucial because:
1. Protects Personal Information
IoT devices gather and store personal data, that ackers may use to steal your identity, conduct illicit transactions, or even blackmail you. Securing your IoT will stop them from their tracks.
2. Prevents Malware Attacks
IoT devices are vulnerable to malware assaults, data leaks, and hacking,. Putting a reliable firewall and antivirus software can prevent such attacks.
To guarantee the efficiency of of IoT networks and apps, users are encourage to do an end-to-end test. The network system must undergo several test to ensure that all parts function together without a hiccup, from the endpoint device to the cloud infrastructure like Azure.
3. Maintains Network Security
Developers take the required precautions to safeguard IoT apps from cross-site scripting (XSS), This script is a security flaw wherein hackers to access your network and other devices and data. Avoid such attacks by using the latest IoT security solutions.
4. Protects IoT Infrastructure
As more homes and businesses adopt IoT devices on their daily operation they are increasingly used in critical resources and infrastructure. A security breach in these systems can have catastrophic consequences and its best to stay ahead of the curve.
Conclusion
There is no denying that Industrial IoT is the future. As more people gain access to the internet, it is critical to provide everyone with increased security. Firewalls are the first line of defense to IoT security and should have better capabilities.
Your smart devices must be protected and kept safe, requiring an IoT firewall. The IoT firewall can stop unauthorized access and defend your personal information from cyber-attacks by regulating the flow to and from your devices.
It might be challenging to access IoT devices protected by a firewall, but you can utilize several safe access methods. SSH, VPNs, and port forwarding are efficient ways to securely and remotely access IoT device behind firewall.
IoT security is necessary to safeguard our private data, fend off malware infections, maintain network security, safeguard IoT infrastructure, and stop DDoS attacks. To protect your data and the devices themselves, it’s crucial to implement robust security measures and keep your IoT devices updated.