Is Chrome Remote Desktop Safe? Protective Measures to Avoid CRD Security Risks
All remote desktop software poses some security risks. In general, Chrome Remote Desktop is a secure solution. It protects your data by using secure SSL connections when establishing a remote session and employs AES encryption to prevent unauthorized users from viewing your information. There are, however, some Chrome Remote Desktop security risks that are especially important when the tool is used in a business setting.
The following article looks at some Chrome Remote Desktop security issues. We also recommend methods for making the tool more secure to better protect your systems and data.
Useful tip:
Security concerns are a notable issue with Chrome Remote Desktop. For assured safety and to protect personal data, opting for an alternative secure remote access software like HelpWire is advisable. HelpWire utilizes top-tier encryption and robust authentication techniques, ensuring secure connections for both support professionals and their remote clients.
Privacy Concerns
When looking at how secure Chrome Remote Desktop is, privacy immediately comes to mind. When establishing a remote session, the target computer must be awake and unlocked. This provides other users with access to the machine without logging in or entering any credentials. Anyone sitting at the console can turn on the screen and watch the activities performed by the remote session. They can also access the apps and information stored on the desktop computer.
Solution: Enable Curtain mode
Curtain mode prevents an individual from observing a remote session by viewing the activity on the desktop machine. Enabling curtain mode requires users to update Windows registry keys or make configuration changes to macOS.
Enabling curtain mode on Windows systems
Option 1: Use the following procedure on Windows devices running the Professional, Enterprise, Ultimate, or Server version of the operating system.
After logging in as an administrator, use Regedit to set the following registry keys:
- • HKEY_LOCAL_MACHINE\Software\Policies\Google\Chrome\RemoteAccess
HostRequireCurtain to 1. - • HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\fDenyTSConnections to 0.
- • HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp\UserAuthentication to 0.
Windows 10 systems need an additional registry key addressed:
- • HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp\SecurityLayer to 1.
All of the previous steps must be completed to enable Curtain mode. If you miss a step, your session may terminate, forcing you to repeat the registry updates.
Option 2: Another option with Windows machines is to run the following long and extensive commands from an elevated command line prompt. These concatenated commands set the registry values and force them to go into effect immediately.
reg add HKLM\Software\Policies\Google\Chrome /v RemoteAccessHostRequireCurtain /d 1 /t REG_DWORD /f && reg add "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /d 0 /t REG_DWORD /f && reg add "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /v SecurityLayer /d 1 /t REG_DWORD /f && reg add "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /v UserAuthentication /d 0 /t REG_DWORD /f && net stop chromoting && net start chromoting
Steps to enable curtain mode for Mac:
Note: Curtain mode is not supported on Mac devices running macOS Big Sur (version 11) or later.
Open a Terminal window using an ID with administrative permission.
Set the default value of RemoteAccessHostRequireCurtain to true by executing the defaults command for the current user and root.
- •
defaults write com.google.Chrome RemoteAccessHostRequireCurtain -boolean true - •
sudo defaults write com.google.Chrome RemoteAccessHostRequireCurtain -boolean true
To restore RemoteAccessHostRequireCurtain, delete the key from the defaults for the current user and root:
- •
defaults delete com.google.Chrome RemoteAccessHostRequireCurtain - •
sudo defaults delete com.google.Chrome RemoteAccessHostRequireCurtain
Potentially Weak Credentials
Deciding if Chrome Remote Desktop is safe depends on the complexity and security of the credentials used to establish the session. A Chrome Remote Desktop connection can be used by a hacker to gain entry to your company’s infrastructure, where they can launch ransomware, monitor activities, and steal data.
By default, a standard Chrome Remote Desktop session is protected by the password of an individual’s Google account. Threat actors use tactics such as man-in-the-middle attacks, brute force attacks, and phishing emails to gain access to credentials with which to compromise Chrome Remote Desktop sessions.
Some remote access tools like TeamViewer, which are designed for business use, can generate a unique string of characters that are used for a single remote session. Chrome does not have this facility, but there are some steps you can take to minimize this Chrome Remote Desktop security vulnerability.
Solution 1: Protect Google account with strong password and 2-Step Verification
Using a strong password and two-factor authentication is a good idea that offers additional protection for your Google account and, by extension, your Chrome Remote Desktop sessions. A strong password is at least 12 characters long and is not easily guessed by potential attackers. You should not share the password with anyone and change it regularly, especially if you think it has been compromised.
In addition to setting a strong password, enable 2-Step Verification for your Google accounts with the following procedure.
- Open the Chrome browser.
- Navigate to the 2-Step Verification.
-
Click Get Started in the pop-up window and follow the prompts to enable 2-Step Verification.
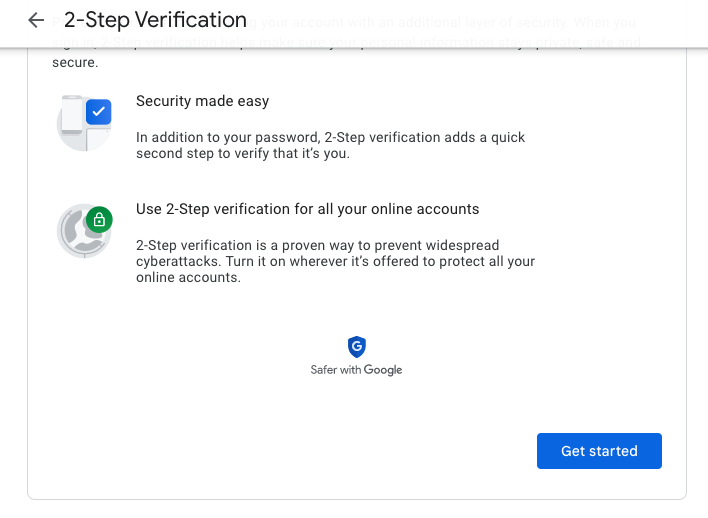
The combination of a strong password and 2-Step Verification improves the security of your Google account and remote desktop sessions.
Solution 2: Set a long and complex PIN
You need to define a PIN code when configuring Chrome Remote Desktop. Google requires you to select a PIN of at least six digits. Setting a longer PIN improves security by making it less vulnerable to attacks by threat actors. If you have already set a Chrome Remote Desktop PIN, you can edit it in the Remote Device section of the interface.
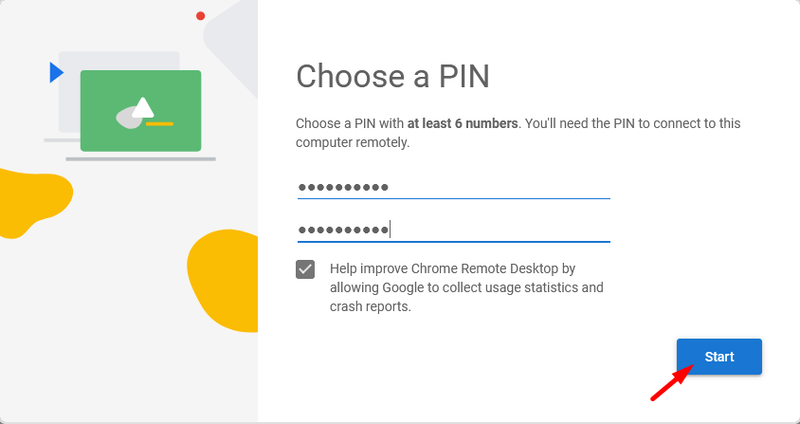
Public WiFi Vulnerability
Using your own device for work or public WiFi networks exposes a Chrome Remote Desktop connection to multiple types of attacks. Typically, you will be connecting through an open firewall port, which is a potential vulnerability hackers can exploit. By identifying the port you are using for the remote desktop connection, hackers have the information they need to launch an attack.
Solution: Use VPN and antivirus software
You can take these two steps to minimize this vulnerability and make sure the Chrome Remote Desktop connection is safe:
- Implement a virtual private network (VPN) on the device you use to establish your Chrome Remote Desktop session. A VPN employs encryption and tunneling technology that creates a secure connection between your machine and the network. The only way to safely use public WiFi for sensitive activities is with a VPN.
- Deploy updated malware and antivirus software on your device and regularly review system logs to look for suspicious activity.

Business users should always use a VPN for remote work before establishing a Chrome Remote Desktop connection to company resources.
Firewall Issues and Compatibility
Many users deploy third-party firewalls to provide protection for their networks and endpoints. A properly configured firewall controls inbound and outbound network traffic to keep your device secure and ensures no unauthorized data exfiltration is being performed.
Unfortunately, Chrome Remote Desktop has known issues with many popular firewall solutions. Remote Desktop solutions more geared toward business users are generally more compatible with firewalls.
Solution: Enable NLA and create firewall exceptions
If you encounter a firewall impacting your ability to connect with Chrome Remote Desktop, you can enable Network Level Authentication (NLA). This parameter can be accessed through Remote Desktop Connection Properties.
You can keep your firewall operational while using Chrome Remote Desktop by creating an exception that allows the connection to be established. This protects your computer by enabling you to access it through your Chrome Remote Desktop session.

Secure Remote Support Software
Make the switch to HelpWire, a more secure alternative to Chrome Remote Desktop, and avoid potential security risks. HelpWire utilizes Auth0, a trusted third-party authentication provider, to ensure safe user logins. All data and connections are protected by 256-bit AES encryption and TLS/SSL protocols.
The platform creates direct peer-to-peer connections between the Operator and the remote Client, bypassing servers wherever possible. If a direct connection isn’t available, AWS servers are used strictly for routing the data, ensuring it remains end-to-end encrypted and anonymized.
HelpWire offers reliable, secure, straightforward, and cost-effective remote access – ideal for professional and personal use.
✔ Multi-platform support – Works on Windows, macOS, and Linux.
✔ No extra costs – Access remotely without additional fees.
✔ Easy setup – No complex server configurations are required.
✔ Unattended access – Connect securely at any time.